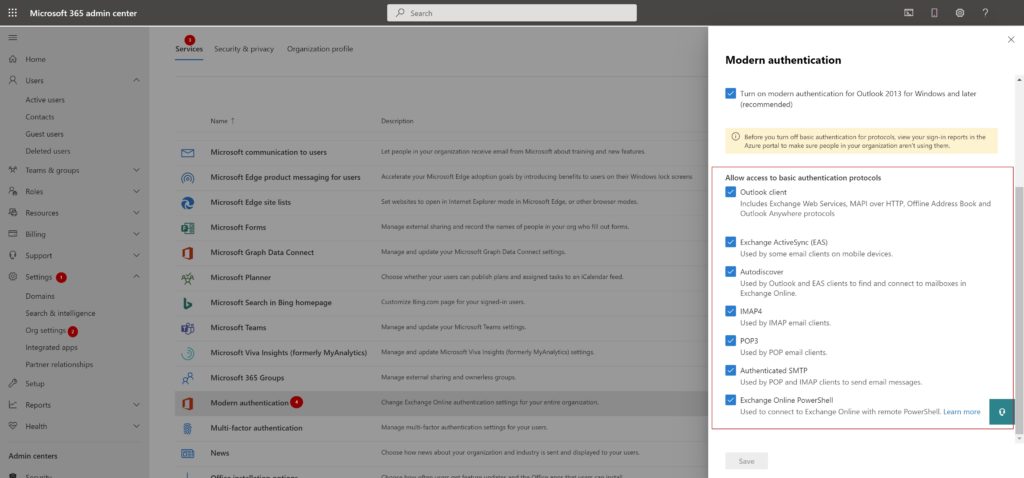
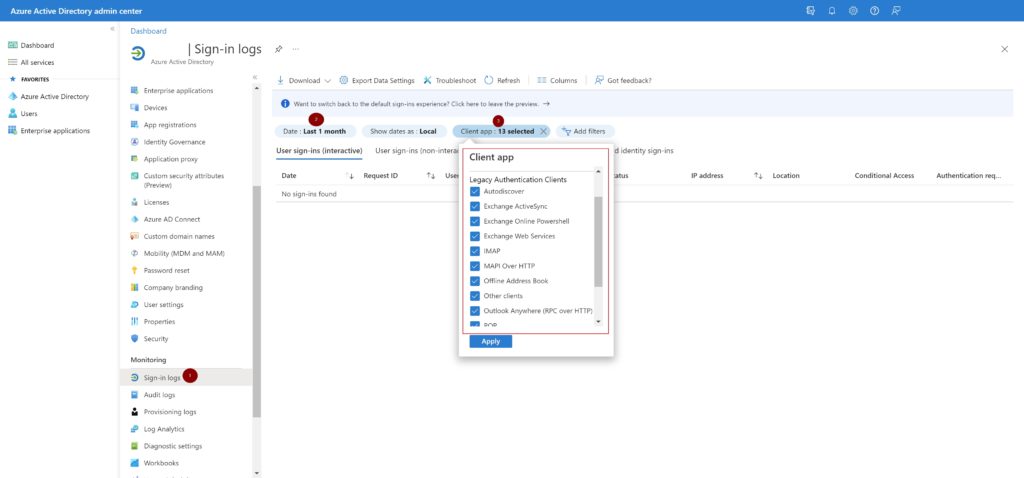
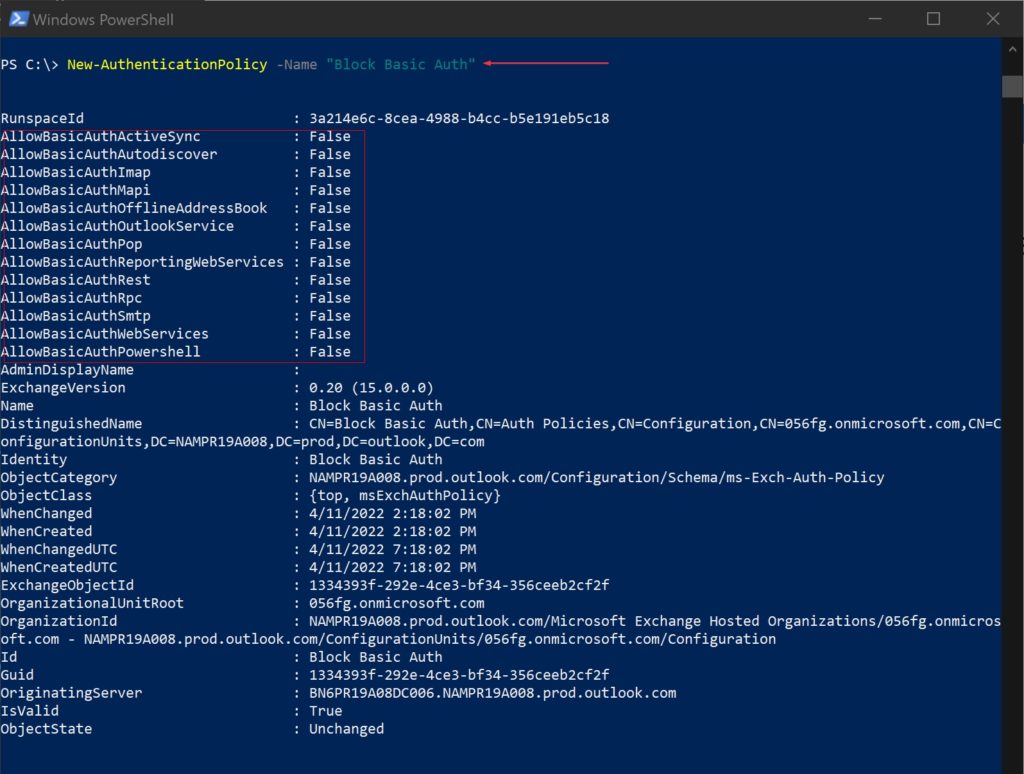
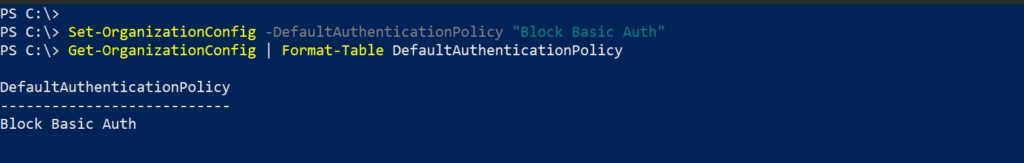
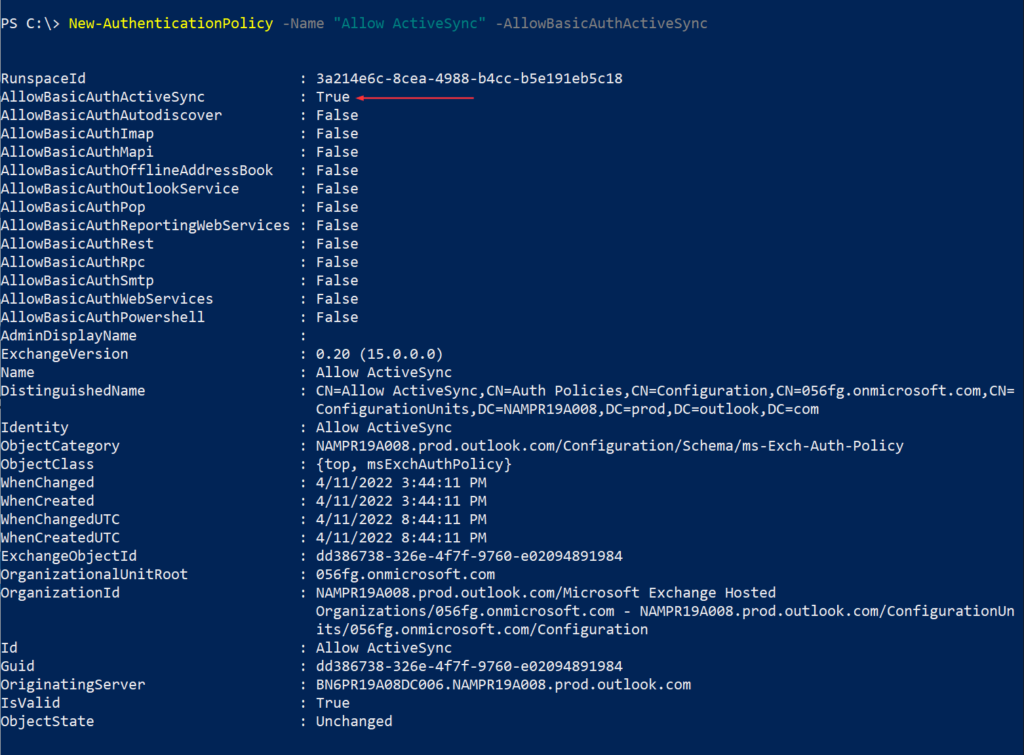
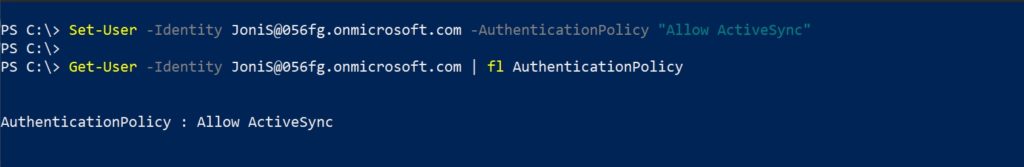
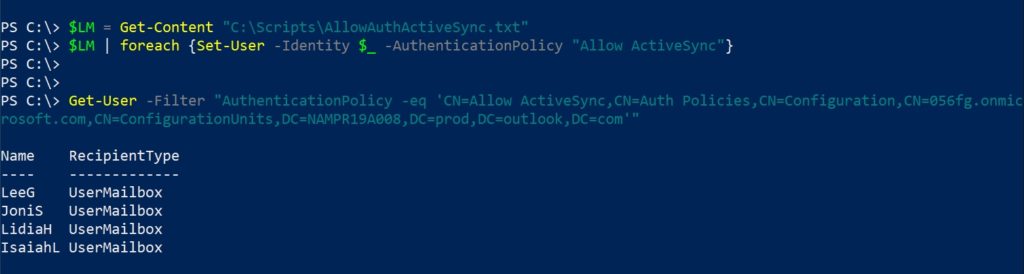
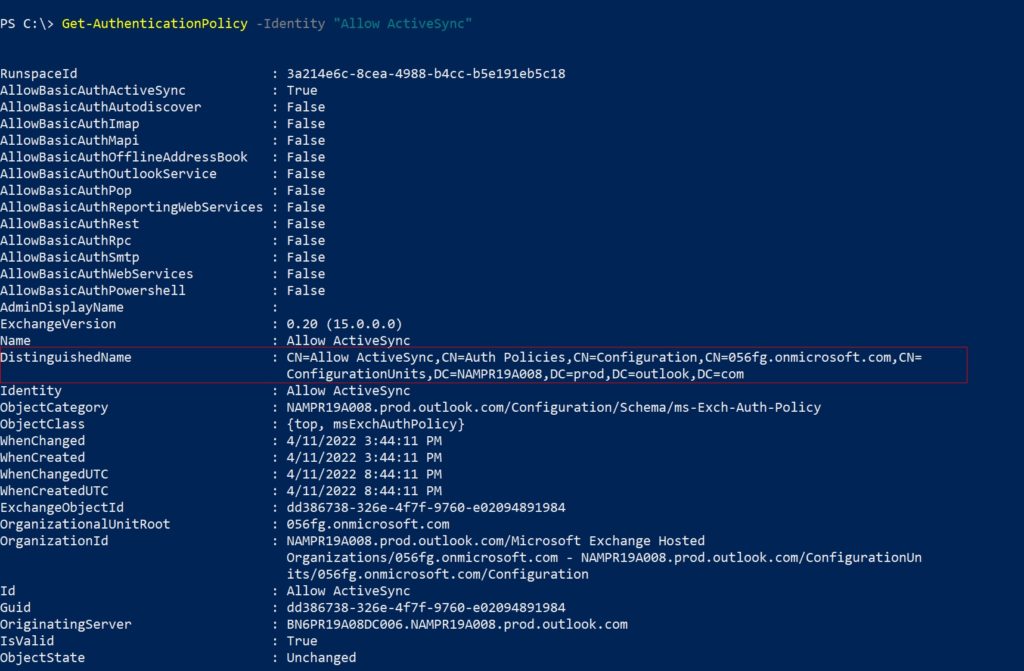
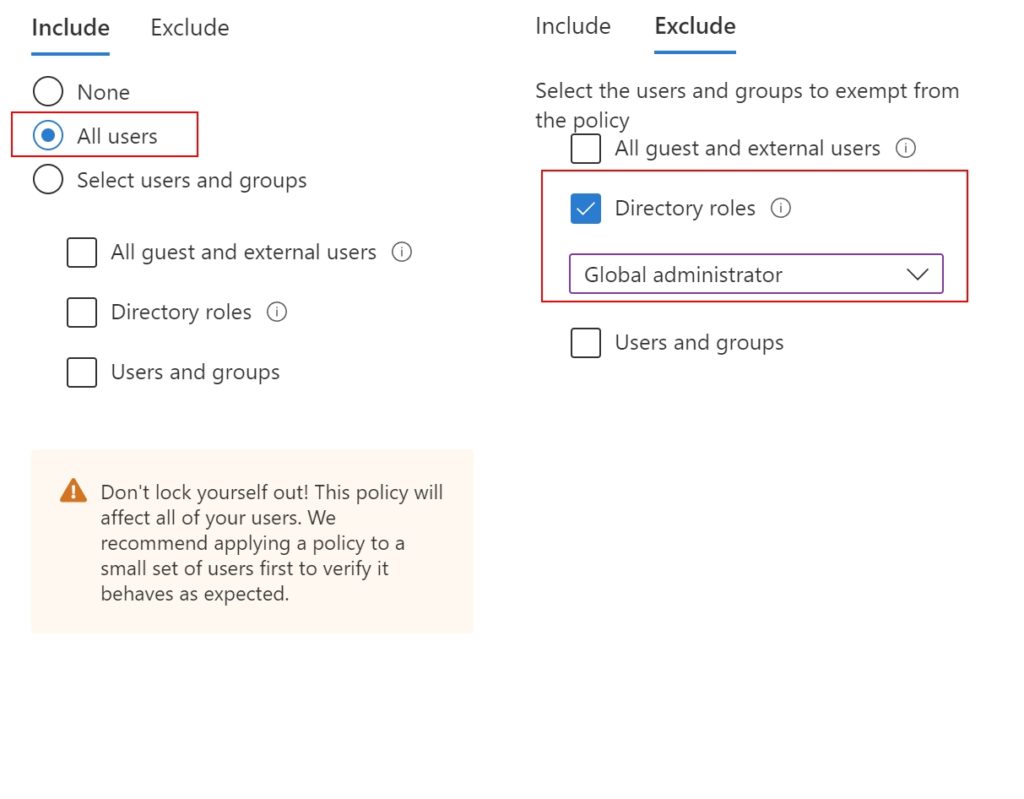
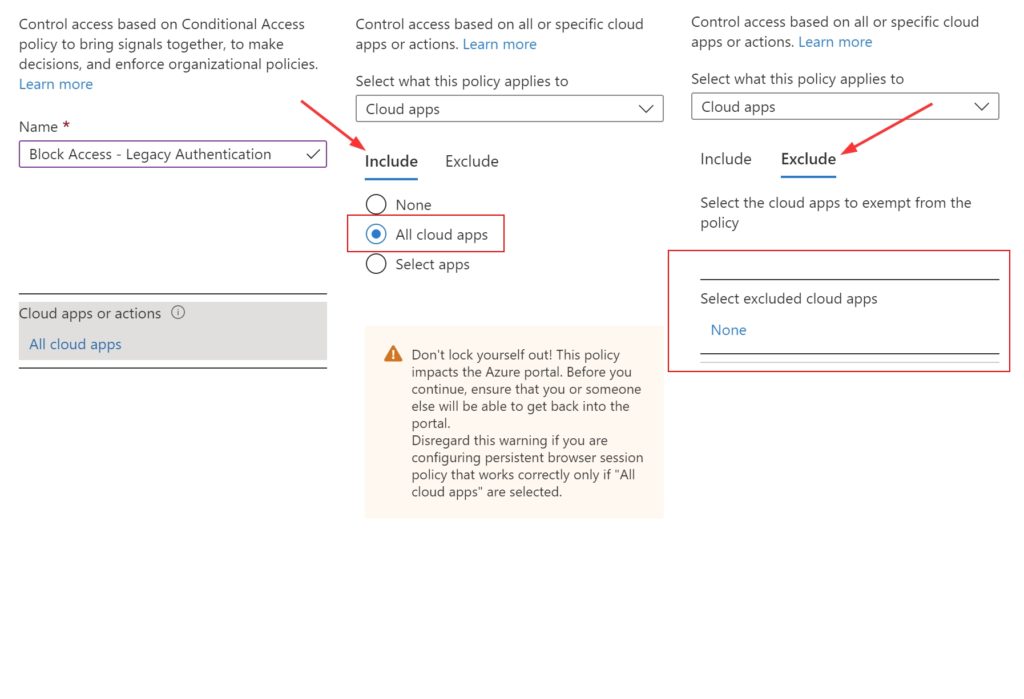
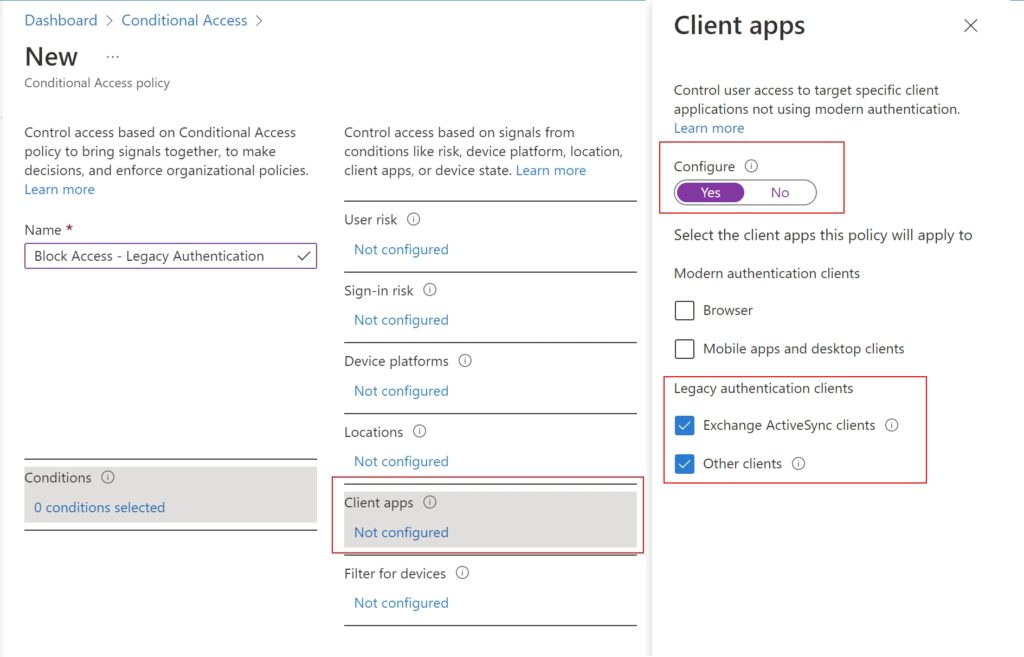
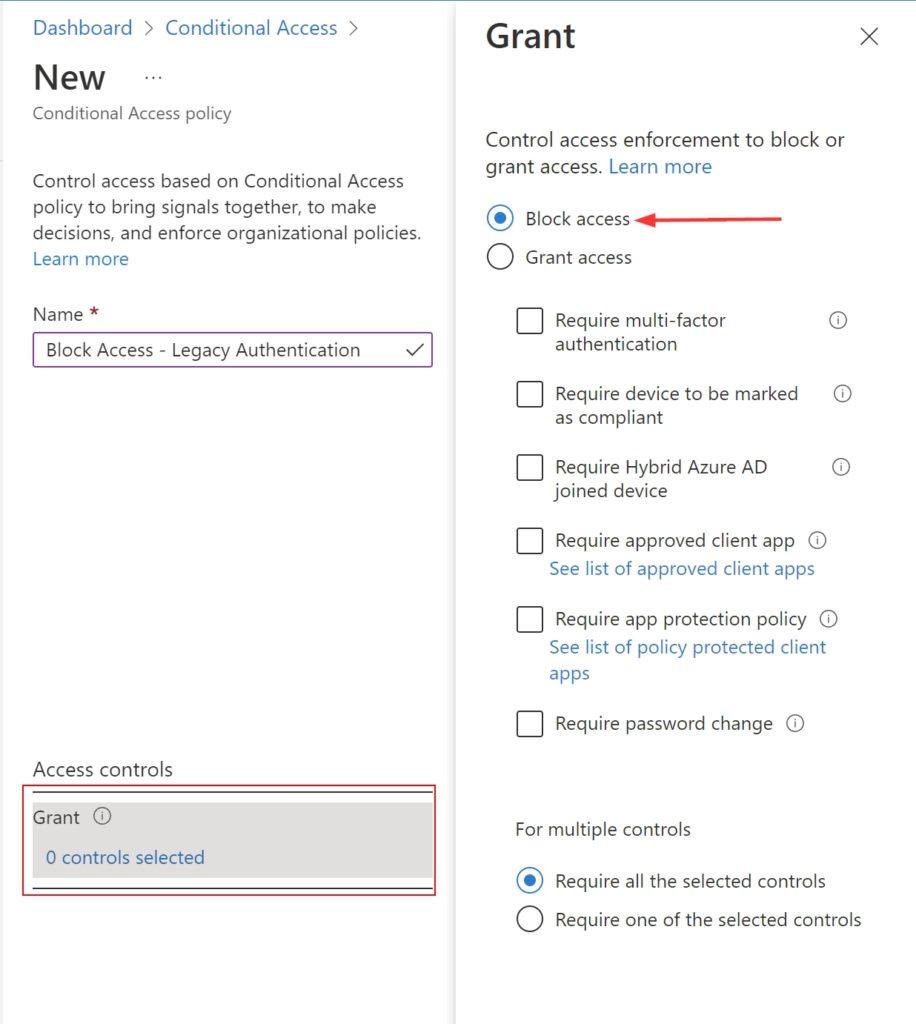
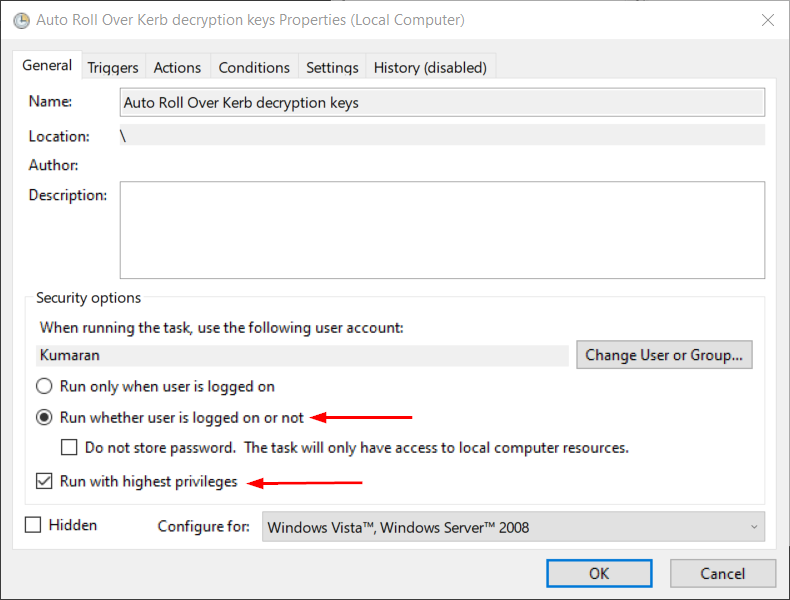
| Scope Name | ID | type | DisplayName |
| AccessReview.Read.All | ebfcd32b-babb-40f4-a14b-42706e83bd28 | Admin | Read all access reviews that user can access |
| AccessReview.ReadWrite.All | e4aa47b9-9a69-4109-82ed-36ec70d85ff1 | Admin | Manage all access reviews that user can access |
| AccessReview.ReadWrite.Membership | 5af8c3f5-baca-439a-97b0-ea58a435e269 | Admin | Manage access reviews for group and app memberships |
| AdministrativeUnit.Read.All | 3361d15d-be43-4de6-b441-3c746d05163d | Admin | Read administrative units |
| AdministrativeUnit.ReadWrite.All | 7b8a2d34-6b3f-4542-a343-54651608ad81 | Admin | Read and write administrative units |
| Agreement.Read.All | af2819c9-df71-4dd3-ade7-4d7c9dc653b7 | Admin | Read all terms of use agreements |
| Agreement.ReadWrite.All | ef4b5d93-3104-4664-9053-a5c49ab44218 | Admin | Read and write all terms of use agreements |
| AgreementAcceptance.Read | 0b7643bb-5336-476f-80b5-18fbfbc91806 | Admin | Read user terms of use acceptance statuses |
| AgreementAcceptance.Read.All | a66a5341-e66e-4897-9d52-c2df58c2bfb9 | Admin | Read terms of use acceptance statuses that user can access |
| APIConnectors.Read.All | 1b6ff35f-31df-4332-8571-d31ea5a4893f | Admin | Read API connectors for authentication flows |
| APIConnectors.ReadWrite.All | c67b52c5-7c69-48b6-9d48-7b3af3ded914 | Admin | Read and write API connectors for authentication flows |
| AppCatalog.ReadWrite.All | 1ca167d5-1655-44a1-8adf-1414072e1ef9 | Admin | Read and write to all app catalogs |
| Application.Read.All | c79f8feb-a9db-4090-85f9-90d820caa0eb | Admin | Read applications |
| Application.ReadWrite.All | bdfbf15f-ee85-4955-8675-146e8e5296b5 | Admin | Read and write all applications |
| AppRoleAssignment.ReadWrite.All | 84bccea3-f856-4a8a-967b-dbe0a3d53a64 | Admin | Manage app permission grants and app role assignments |
| Approval.Read.All | 1196552e-b226-4363-b01e-b8901fe10a11 | Admin | Read approvals |
| Approval.ReadWrite.All | 1d3d0bc7-4b3a-427a-ae9f-6de4e1edc95f | Admin | Read and write approvals |
| AttackSimulation.Read.All | 104a7a4b-ca76-4677-b7e7-2f4bc482f381 | Admin | Read attack simulation data of an organization |
| AuditLog.Read.All | e4c9e354-4dc5-45b8-9e7c-e1393b0b1a20 | Admin | Read audit log data |
| AuthenticationContext.Read.All | 57b030f1-8c35-469c-b0d9-e4a077debe70 | Admin | Read all authentication context information |
| AuthenticationContext.ReadWrite.All | ba6d575a-1344-4516-b777-1404f5593057 | Admin | Read and write all authentication context information |
| BitlockerKey.Read.All | b27a61ec-b99c-4d6a-b126-c4375d08ae30 | Admin | Read BitLocker keys |
| BitlockerKey.ReadBasic.All | 5a107bfc-4f00-4e1a-b67e-66451267bc68 | Admin | Read BitLocker keys basic information |
| Channel.Create | 101147cf-4178-4455-9d58-02b5c164e759 | Admin | Create channels |
| Channel.Delete.All | cc83893a-e232-4723-b5af-bd0b01bcfe65 | Admin | Delete channels |
| ChannelMember.Read.All | 2eadaff8-0bce-4198-a6b9-2cfc35a30075 | Admin | Read the members of channels |
| ChannelMember.ReadWrite.All | 0c3e411a-ce45-4cd1-8f30-f99a3efa7b11 | Admin | Add and remove members from channels |
| ChannelMessage.Read.All | 767156cb-16ae-4d10-8f8b-41b657c8c8c8 | Admin | Read user channel messages |
| ChannelMessage.ReadWrite | 5922d31f-46c8-4404-9eaf-2117e390a8a4 | Admin | Read and write user channel messages |
| ChannelSettings.Read.All | 233e0cf1-dd62-48bc-b65b-b38fe87fcf8e | Admin | Read the names, descriptions, and settings of channels |
| ChannelSettings.ReadWrite.All | d649fb7c-72b4-4eec-b2b4-b15acf79e378 | Admin | Read and write the names, descriptions, and settings of channels |
| ChatMember.Read | c5a9e2b1-faf6-41d4-8875-d381aa549b24 | Admin | Read the members of chats |
| ChatMember.ReadWrite | dea13482-7ea6-488f-8b98-eb5bbecf033d | Admin | Add and remove members from chats |
| CloudPC.ReadWrite.All | 9d77138f-f0e2-47ba-ab33-cd246c8b79d1 | Admin | Read and write Cloud PCs |
| ConsentRequest.Read.All | f3bfad56-966e-4590-a536-82ecf548ac1e | Admin | Read consent requests |
| ConsentRequest.ReadWrite.All | 497d9dfa-3bd1-481a-baab-90895e54568c | Admin | Read and write consent requests |
| CrossTenantInformation.ReadBasic.All | 81594d25-e88e-49cf-ac8c-fecbff49f994 | Admin | Read cross-tenant basic information |
| CrossTenantUserProfileSharing.Read | cb1ba48f-d22b-4325-a07f-74135a62ee41 | Admin | Read shared cross-tenant user profile and export data |
| CrossTenantUserProfileSharing.Read.All | 759dcd16-3c90-463c-937e-abf89f991c18 | Admin | Read all shared cross-tenant user profiles and export their data |
| CrossTenantUserProfileSharing.ReadWrite | eed0129d-dc60-4f30-8641-daf337a39ffd | Admin | Read shared cross-tenant user profile and export or delete data |
| CrossTenantUserProfileSharing.ReadWrite.All | 64dfa325-cbf8-48e3-938d-51224a0cac01 | Admin | Read all shared cross-tenant user profiles and export or delete their data |
| CustomAuthenticationExtension.Read.All | b2052569-c98c-4f36-a5fb-43e5c111e6d0 | Admin | Read your oganization’s custom authentication extensions |
| CustomAuthenticationExtension.ReadWrite.All | 8dfcf82f-15d0-43b3-bc78-a958a13a5792 | Admin | Read and write your organization’s custom authentication extensions |
| CustomSecAttributeAssignment.Read.All | b46ffa80-fe3d-4822-9a1a-c200932d54d0 | Admin | Read custom security attribute assignments |
| CustomSecAttributeAssignment.ReadWrite.All | ca46335e-8453-47cd-a001-8459884efeae | Admin | Read and write custom security attribute assignments |
| CustomSecAttributeDefinition.Read.All | ce026878-a0ff-4745-a728-d4fedd086c07 | Admin | Read custom security attribute definitions |
| CustomSecAttributeDefinition.ReadWrite.All | 8b0160d4-5743-482b-bb27-efc0a485ca4a | Admin | Read and write custom security attribute definitions |
| DelegatedAdminRelationship.Read.All | 0c0064ea-477b-4130-82a5-4c2cc4ff68aa | Admin | Read Delegated Admin relationships with customers |
| DelegatedAdminRelationship.ReadWrite.All | 885f682f-a990-4bad-a642-36736a74b0c7 | Admin | Manage Delegated Admin relationships with customers |
| DelegatedPermissionGrant.ReadWrite.All | 41ce6ca6-6826-4807-84f1-1c82854f7ee5 | Admin | Manage all delegated permission grants |
| Device.Read.All | 951183d1-1a61-466f-a6d1-1fde911bfd95 | Admin | Read all devices |
| DeviceManagementApps.Read.All | 4edf5f54-4666-44af-9de9-0144fb4b6e8c | Admin | Read Microsoft Intune apps |
| DeviceManagementApps.ReadWrite.All | 7b3f05d5-f68c-4b8d-8c59-a2ecd12f24af | Admin | Read and write Microsoft Intune apps |
| DeviceManagementConfiguration.Read.All | f1493658-876a-4c87-8fa7-edb559b3476a | Admin | Read Microsoft Intune Device Configuration and Policies |
| DeviceManagementConfiguration.ReadWrite.All | 0883f392-0a7a-443d-8c76-16a6d39c7b63 | Admin | Read and write Microsoft Intune Device Configuration and Policies |
| DeviceManagementManagedDevices.PrivilegedOperations.All | 3404d2bf-2b13-457e-a330-c24615765193 | Admin | Perform user-impacting remote actions on Microsoft Intune devices |
| DeviceManagementManagedDevices.Read.All | 314874da-47d6-4978-88dc-cf0d37f0bb82 | Admin | Read Microsoft Intune devices |
| DeviceManagementManagedDevices.ReadWrite.All | 44642bfe-8385-4adc-8fc6-fe3cb2c375c3 | Admin | Read and write Microsoft Intune devices |
| DeviceManagementRBAC.Read.All | 49f0cc30-024c-4dfd-ab3e-82e137ee5431 | Admin | Read Microsoft Intune RBAC settings |
| DeviceManagementRBAC.ReadWrite.All | 0c5e8a55-87a6-4556-93ab-adc52c4d862d | Admin | Read and write Microsoft Intune RBAC settings |
| DeviceManagementServiceConfig.Read.All | 8696daa5-bce5-4b2e-83f9-51b6defc4e1e | Admin | Read Microsoft Intune configuration |
| DeviceManagementServiceConfig.ReadWrite.All | 662ed50a-ac44-4eef-ad86-62eed9be2a29 | Admin | Read and write Microsoft Intune configuration |
| Directory.AccessAsUser.All | 0e263e50-5827-48a4-b97c-d940288653c7 | Admin | Access directory as the signed in user |
| Directory.Read.All | 06da0dbc-49e2-44d2-8312-53f166ab848a | Admin | Read directory data |
| Directory.ReadWrite.All | c5366453-9fb0-48a5-a156-24f0c49a4b84 | Admin | Read and write directory data |
| Directory.Write.Restricted | cba5390f-ed6a-4b7f-b657-0efc2210ed20 | Admin | Manage restricted resources in the directory |
| DirectoryRecommendations.Read.All | 34d3bd24-f6a6-468c-b67c-0c365c1d6410 | Admin | Read Azure AD recommendations |
| DirectoryRecommendations.ReadWrite.All | f37235e8-90a0-4189-93e2-e55b53867ccd | Admin | Read and update Azure AD recommendations |
| Domain.Read.All | 2f9ee017-59c1-4f1d-9472-bd5529a7b311 | Admin | Read domains. |
| Domain.ReadWrite.All | 0b5d694c-a244-4bde-86e6-eb5cd07730fe | Admin | Read and write domains |
| eDiscovery.Read.All | 99201db3-7652-4d5a-809a-bdb94f85fe3c | Admin | Read all eDiscovery objects |
| eDiscovery.ReadWrite.All | acb8f680-0834-4146-b69e-4ab1b39745ad | Admin | Read and write all eDiscovery objects |
| EduAdministration.Read | 8523895c-6081-45bf-8a5d-f062a2f12c9f | Admin | Read education app settings |
| EduAdministration.ReadWrite | 63589852-04e3-46b4-bae9-15d5b1050748 | Admin | Manage education app settings |
| EduAssignments.Read | 091460c9-9c4a-49b2-81ef-1f3d852acce2 | Admin | Read users’ class assignments and their grades |
| EduAssignments.ReadBasic | c0b0103b-c053-4b2e-9973-9f3a544ec9b8 | Admin | Read users’ class assignments without grades |
| EduAssignments.ReadWrite | 2f233e90-164b-4501-8bce-31af2559a2d3 | Admin | Read and write users’ class assignments and their grades |
| EduAssignments.ReadWriteBasic | 2ef770a1-622a-47c4-93ee-28d6adbed3a0 | Admin | Read and write users’ class assignments without grades |
| EduRoster.Read | a4389601-22d9-4096-ac18-36a927199112 | Admin | Read users’ view of the roster |
| EduRoster.ReadBasic | 5d186531-d1bf-4f07-8cea-7c42119e1bd9 | Admin | Read a limited subset of users’ view of the roster |
| EduRoster.ReadWrite | 359e19a6-e3fa-4d7f-bcab-d28ec592b51e | Admin | Read and write users’ view of the roster |
| EntitlementManagement.Read.All | 5449aa12-1393-4ea2-a7c7-d0e06c1a56b2 | Admin | Read all entitlement management resources |
| EntitlementManagement.ReadWrite.All | ae7a573d-81d7-432b-ad44-4ed5c9d89038 | Admin | Read and write entitlement management resources |
| EventListener.Read.All | f7dd3bed-5eec-48da-bc73-1c0ef50bc9a1 | Admin | Read your organization’s authentication event listeners |
| EventListener.ReadWrite.All | d11625a6-fe21-4fc6-8d3d-063eba5525ad | Admin | Read and write your organization’s authentication event listeners |
| ExternalConnection.Read.All | a38267a5-26b6-4d76-9493-935b7599116b | Admin | Read all external connections |
| ExternalConnection.ReadWrite.All | bbbbd9b3-3566-4931-ac37-2b2180d9e334 | Admin | Read and write all external connections |
| ExternalConnection.ReadWrite.OwnedBy | 4082ad95-c812-4f02-be92-780c4c4f1830 | Admin | Read and write external connections |
| ExternalItem.Read.All | 922f9392-b1b7-483c-a4be-0089be7704fb | Admin | Read items in external datasets |
| ExternalItem.ReadWrite.All | b02c54f8-eb48-4c50-a9f0-a149e5a2012f | Admin | Read and write all external items |
| ExternalItem.ReadWrite.OwnedBy | 4367b9d7-cee7-4995-853c-a0bdfe95c1f9 | Admin | Read and write external items |
| Group.Read.All | 5f8c59db-677d-491f-a6b8-5f174b11ec1d | Admin | Read all groups |
| Group.ReadWrite.All | 4e46008b-f24c-477d-8fff-7bb4ec7aafe0 | Admin | Read and write all groups |
| GroupMember.Read.All | bc024368-1153-4739-b217-4326f2e966d0 | Admin | Read group memberships |
| GroupMember.ReadWrite.All | f81125ac-d3b7-4573-a3b2-7099cc39df9e | Admin | Read and write group memberships |
| IdentityProvider.Read.All | 43781733-b5a7-4d1b-98f4-e8edff23e1a9 | Admin | Read identity providers |
| IdentityProvider.ReadWrite.All | f13ce604-1677-429f-90bd-8a10b9f01325 | Admin | Read and write identity providers |
| IdentityRiskEvent.Read.All | 8f6a01e7-0391-4ee5-aa22-a3af122cef27 | Admin | Read identity risk event information |
| IdentityRiskEvent.ReadWrite.All | 9e4862a5-b68f-479e-848a-4e07e25c9916 | Admin | Read and write risk event information |
| IdentityRiskyServicePrincipal.Read.All | ea5c4ab0-5a73-4f35-8272-5d5337884e5d | Admin | Read all identity risky service principal information |
| IdentityRiskyServicePrincipal.ReadWrite.All | bb6f654c-d7fd-4ae3-85c3-fc380934f515 | Admin | Read and write all identity risky service principal information |
| IdentityRiskyUser.Read.All | d04bb851-cb7c-4146-97c7-ca3e71baf56c | Admin | Read identity risky user information |
| IdentityRiskyUser.ReadWrite.All | e0a7cdbb-08b0-4697-8264-0069786e9674 | Admin | Read and write risky user information |
| IdentityUserFlow.Read.All | 2903d63d-4611-4d43-99ce-a33f3f52e343 | Admin | Read all identity user flows |
| IdentityUserFlow.ReadWrite.All | 281892cc-4dbf-4e3a-b6cc-b21029bb4e82 | Admin | Read and write all identity user flows |
| LearningContent.Read.All | ea4c1fd9-6a9f-4432-8e5d-86e06cc0da77 | Admin | Read learning content |
| LearningContent.ReadWrite.All | 53cec1c4-a65f-4981-9dc1-ad75dbf1c077 | Admin | Managelearningcontent |
| LearningProvider.Read | dd8ce36f-9245-45ea-a99e-8ac398c22861 | Admin | Read learning provider |
| LearningProvider.ReadWrite | 40c2eb57-abaf-49f5-9331-e90fd01f7130 | Admin | Managelearningprovider |
| LicenseAssignment.ReadWrite.All | f55016cc-149c-447e-8f21-7cf3ec1d6350 | Admin | Manage all license assignments |
| LifecycleWorkflows.Read.All | 9bcb9916-765a-42af-bf77-02282e26b01a | Admin | Read all lifecycle workflows resources |
| LifecycleWorkflows.ReadWrite.All | 84b9d731-7db8-4454-8c90-fd9e95350179 | Admin | Read and write all lifecycle workflows resources |
| ManagedTenants.Read.All | dc34164e-6c4a-41a0-be89-3ae2fbad7cd3 | Admin | Read all managed tenant information |
| ManagedTenants.ReadWrite.All | b31fa710-c9b3-4d9e-8f5e-8036eecddab9 | Admin | Read and write all managed tenant information |
| Member.Read.Hidden | f6a3db3e-f7e8-4ed2-a414-557c8c9830be | Admin | Read hidden memberships |
| OnlineMeetingRecording.Read.All | 190c2bb6-1fdd-4fec-9aa2-7d571b5e1fe3 | Admin | Read all recordings of online meetings. |
| OnlineMeetingTranscript.Read.All | 30b87d18-ebb1-45db-97f8-82ccb1f0190c | Admin | Read all transcripts of online meetings. |
| OnPremisesPublishingProfiles.ReadWrite.All | 8c4d5184-71c2-4bf8-bb9d-bc3378c9ad42 | Admin | Manage on-premises published resources |
| Organization.Read.All | 4908d5b9-3fb2-4b1e-9336-1888b7937185 | Admin | Read organization information |
| Organization.ReadWrite.All | 46ca0847-7e6b-426e-9775-ea810a948356 | Admin | Read and write organization information |
| OrgContact.Read.All | 08432d1b-5911-483c-86df-7980af5cdee0 | Admin | Read organizational contacts |
| People.Read.All | b89f9189-71a5-4e70-b041-9887f0bc7e4a | Admin | Read all users’ relevant people lists |
| Place.Read.All | cb8f45a0-5c2e-4ea1-b803-84b870a7d7ec | Admin | Read all company places |
| Place.ReadWrite.All | 4c06a06a-098a-4063-868e-5dfee3827264 | Admin | Read and write organization places |
| Policy.Read.All | 572fea84-0151-49b2-9301-11cb16974376 | Admin | Read your organization’s policies |
| Policy.Read.PermissionGrant | 414de6ea-2d92-462f-b120-6e2a809a6d01 | Admin | Read consent and permission grant policies |
| Policy.ReadWrite.AccessReview | 4f5bc9c8-ea54-4772-973a-9ca119cb0409 | Admin | Read and write your organization’s directory access review default policy |
| Policy.ReadWrite.ApplicationConfiguration | b27add92-efb2-4f16-84f5-8108ba77985c | Admin | Read and write your organization’s application configuration policies |
| Policy.ReadWrite.AuthenticationFlows | edb72de9-4252-4d03-a925-451deef99db7 | Admin | Read and write authentication flow policies |
| Policy.ReadWrite.AuthenticationMethod | 7e823077-d88e-468f-a337-e18f1f0e6c7c | Admin | Read and write authentication method policies |
| Policy.ReadWrite.Authorization | edd3c878-b384-41fd-95ad-e7407dd775be | Admin | Read and write your organization’s authorization policy |
| Policy.ReadWrite.ConditionalAccess | ad902697-1014-4ef5-81ef-2b4301988e8c | Admin | Read and write your organization’s conditional access policies |
| Policy.ReadWrite.ConsentRequest | 4d135e65-66b8-41a8-9f8b-081452c91774 | Admin | Read and write consent request policy |
| Policy.ReadWrite.CrossTenantAccess | 014b43d0-6ed4-4fc6-84dc-4b6f7bae7d85 | Admin | Read and write your organization’s cross tenant access policies |
| Policy.ReadWrite.DeviceConfiguration | 40b534c3-9552-4550-901b-23879c90bcf9 | Admin | Read and write your organization’s device configuration policies |
| Policy.ReadWrite.FeatureRollout | 92a38652-f13b-4875-bc77-6e1dbb63e1b2 | Admin | Read and write your organization’s feature rollout policies |
| Policy.ReadWrite.MobilityManagement | a8ead177-1889-4546-9387-f25e658e2a79 | Admin | Read and write your organization’s mobility management policies |
| Policy.ReadWrite.PermissionGrant | 2672f8bb-fd5e-42e0-85e1-ec764dd2614e | Admin | Manage consent and permission grant policies |
| Policy.ReadWrite.TrustFramework | cefba324-1a70-4a6e-9c1d-fd670b7ae392 | Admin | Read and write your organization’s trust framework policies |
| PrintConnector.Read.All | d69c2d6d-4f72-4f99-a6b9-663e32f8cf68 | Admin | Read print connectors |
| PrintConnector.ReadWrite.All | 79ef9967-7d59-4213-9c64-4b10687637d8 | Admin | Read and write print connectors |
| Printer.Create | 90c30bed-6fd1-4279-bf39-714069619721 | Admin | Register printers |
| Printer.FullControl.All | 93dae4bd-43a1-4a23-9a1a-92957e1d9121 | Admin | Register, read, update, and unregister printers |
| Printer.Read.All | 3a736c8a-018e-460a-b60c-863b2683e8bf | Admin | Read printers |
| Printer.ReadWrite.All | 89f66824-725f-4b8f-928e-e1c5258dc565 | Admin | Read and update printers |
| PrinterShare.ReadWrite.All | 06ceea37-85e2-40d7-bec3-91337a46038f | Admin | Read and write printer shares |
| PrintJob.Read.All | afdd6933-a0d8-40f7-bd1a-b5d778e8624b | Admin | Read print jobs |
| PrintJob.ReadBasic.All | 04ce8d60-72ce-4867-85cf-6d82f36922f3 | Admin | Read basic information of print jobs |
| PrintJob.ReadWrite.All | 036b9544-e8c5-46ef-900a-0646cc42b271 | Admin | Read and write print jobs |
| PrintJob.ReadWriteBasic.All | 3a0db2f6-0d2a-4c19-971b-49109b19ad3d | Admin | Read and write basic information of print jobs |
| PrintSettings.Read.All | 490f32fd-d90f-4dd7-a601-ff6cdc1a3f6c | Admin | Read tenant-wide print settings |
| PrintSettings.ReadWrite.All | 9ccc526a-c51c-4e5c-a1fd-74726ef50b8f | Admin | Read and write tenant-wide print settings |
| PrivilegedAccess.Read.AzureAD | b3a539c9-59cb-4ad5-825a-041ddbdc2bdb | Admin | Read privileged access to Azure AD |
| PrivilegedAccess.Read.AzureADGroup | d329c81c-20ad-4772-abf9-3f6fdb7e5988 | Admin | Read privileged access to Azure AD groups |
| PrivilegedAccess.Read.AzureResources | 1d89d70c-dcac-4248-b214-903c457af83a | Admin | Read privileged access to Azure resources |
| PrivilegedAccess.ReadWrite.AzureAD | 3c3c74f5-cdaa-4a97-b7e0-4e788bfcfb37 | Admin | Read and write privileged access to Azure AD |
| PrivilegedAccess.ReadWrite.AzureADGroup | 32531c59-1f32-461f-b8df-6f8a3b89f73b | Admin | Read and write privileged access to Azure AD groups |
| PrivilegedAccess.ReadWrite.AzureResources | a84a9652-ffd3-496e-a991-22ba5529156a | Admin | Read and write privileged access to Azure resources |
| ProgramControl.Read.All | c492a2e1-2f8f-4caa-b076-99bbf6e40fe4 | Admin | Read all programs that user can access |
| ProgramControl.ReadWrite.All | 50fd364f-9d93-4ae1-b170-300e87cccf84 | Admin | Manage all programs that user can access |
| RecordsManagement.Read.All | 07f995eb-fc67-4522-ad66-2b8ca8ea3efd | Admin | Read Records Management configuration,labels, and policies |
| RecordsManagement.ReadWrite.All | f2833d75-a4e6-40ab-86d4-6dfe73c97605 | Admin | Read and write Records Management configuration, labels, and policies |
| Reports.Read.All | 02e97553-ed7b-43d0-ab3c-f8bace0d040c | Admin | Read all usage reports |
| ReportSettings.Read.All | 84fac5f4-33a9-4100-aa38-a20c6d29e5e7 | Admin | Read admin report settings |
| ReportSettings.ReadWrite.All | b955410e-7715-4a88-a940-dfd551018df3 | Admin | Read and write admin report settings |
| RoleAssignmentSchedule.Read.Directory | 344a729c-0285-42c6-9014-f12b9b8d6129 | Admin | Read all active role assignments for your company’s directory |
| RoleAssignmentSchedule.ReadWrite.Directory | 8c026be3-8e26-4774-9372-8d5d6f21daff | Admin | Read, update, and delete all active role assignments for your company’s directory |
| RoleEligibilitySchedule.Read.Directory | eb0788c2-6d4e-4658-8c9e-c0fb8053f03d | Admin | Read all eligible role assignments for your company’s directory |
| RoleEligibilitySchedule.ReadWrite.Directory | 62ade113-f8e0-4bf9-a6ba-5acb31db32fd | Admin | Read, update, and delete all eligible role assignments for your company’s directory |
| RoleManagement.Read.All | 48fec646-b2ba-4019-8681-8eb31435aded | Admin | Read role management data for all RBAC providers |
| RoleManagement.Read.CloudPC | 9619b88a-8a25-48a7-9571-d23be0337a79 | Admin | Read Cloud PC RBAC settings |
| RoleManagement.Read.Directory | 741c54c3-0c1e-44a1-818b-3f97ab4e8c83 | Admin | Read directory RBAC settings |
| RoleManagement.ReadWrite.CloudPC | 501d06f8-07b8-4f18-b5c6-c191a4af7a82 | Admin | Read and write Cloud PC RBAC settings |
| RoleManagement.ReadWrite.Directory | d01b97e9-cbc0-49fe-810a-750afd5527a3 | Admin | Read and write directory RBAC settings |
| RoleManagementPolicy.Read.Directory | 3de2cdbe-0ff5-47d5-bdee-7f45b4749ead | Admin | Read all policies for privileged role assignments of your company’s directory |
| RoleManagementPolicy.ReadWrite.Directory | 1ff1be21-34eb-448c-9ac9-ce1f506b2a68 | Admin | Read, update, and delete all policies for privileged role assignments of your company’s directory |
| Schedule.Read.All | fccf6dd8-5706-49fa-811f-69e2e1b585d0 | Admin | Read user schedule items |
| Schedule.ReadWrite.All | 63f27281-c9d9-4f29-94dd-6942f7f1feb0 | Admin | Read and write user schedule items |
| SearchConfiguration.Read.All | 7d307522-aa38-4cd0-bd60-90c6f0ac50bd | Admin | Read your organization’s search configuration |
| SearchConfiguration.ReadWrite.All | b1a7d408-cab0-47d2-a2a5-a74a3733600d | Admin | Read and write your organization’s search configuration |
| SecurityActions.Read.All | 1638cddf-07a4-4de2-8645-69c96cacad73 | Admin | Read your organization’s security actions |
| SecurityActions.ReadWrite.All | dc38509c-b87d-4da0-bd92-6bec988bac4a | Admin | Read and update your organization’s security actions |
| SecurityAlert.Read.All | bc257fb8-46b4-4b15-8713-01e91bfbe4ea | Admin | Read all security alerts |
| SecurityAlert.ReadWrite.All | 471f2a7f-2a42-4d45-a2bf-594d0838070d | Admin | Read and write to all security alerts |
| SecurityEvents.Read.All | 64733abd-851e-478a-bffb-e47a14b18235 | Admin | Read your organizations security events |
| SecurityEvents.ReadWrite.All | 6aedf524-7e1c-45a7-bd76-ded8cab8d0fc | Admin | Read and update your organizations security events |
| SecurityIncident.Read.All | b9abcc4f-94fc-4457-9141-d20ce80ec952 | Admin | Read incidents |
| SecurityIncident.ReadWrite.All | 128ca929-1a19-45e6-a3b8-435ec44a36ba | Admin | Read and write to incidents |
| ServiceHealth.Read.All | 55896846-df78-47a7-aa94-8d3d4442ca7f | Admin | Read service health |
| ServiceMessage.Read.All | eda39fa6-f8cf-4c3c-a909-432c683e4c9b | Admin | Read service announcement messages |
| ServiceMessageViewpoint.Write | 636e1b0b-1cc2-4b1c-9aa9-4eeed9b9761b | Admin | Update user status on service announcement messages |
| ServicePrincipalEndpoint.Read.All | 9f9ce928-e038-4e3b-8faf-7b59049a8ddc | Admin | Read service principal endpoints |
| ServicePrincipalEndpoint.ReadWrite.All | 7297d82c-9546-4aed-91df-3d4f0a9b3ff0 | Admin | Read and update service principal endpoints |
| SharePointTenantSettings.Read.All | 2ef70e10-5bfd-4ede-a5f6-67720500b258 | Admin | Read SharePoint and OneDrive tenant settings |
| SharePointTenantSettings.ReadWrite.All | aa07f155-3612-49b8-a147-6c590df35536 | Admin | Read and change SharePoint and OneDrive tenant settings |
| Sites.FullControl.All | 5a54b8b3-347c-476d-8f8e-42d5c7424d29 | Admin | Have full control of all site collections |
| SubjectRightsRequest.Read.All | 9c3af74c-fd0f-4db4-b17a-71939e2a9d77 | Admin | Read subject rights requests |
| SubjectRightsRequest.ReadWrite.All | 2b8fcc74-bce1-4ae3-a0e8-60c53739299d | Admin | Read and write subject rights requests |
| Subscription.Read.All | 5f88184c-80bb-4d52-9ff2-757288b2e9b7 | Admin | Read all webhook subscriptions |
| TeamMember.Read.All | 2497278c-d82d-46a2-b1ce-39d4cdde5570 | Admin | Read the members of teams |
| TeamMember.ReadWrite.All | 4a06efd2-f825-4e34-813e-82a57b03d1ee | Admin | Add and remove members from teams |
| TeamMember.ReadWriteNonOwnerRole.All | 2104a4db-3a2f-4ea0-9dba-143d457dc666 | Admin | Add and remove members with non-owner role for all teams |
| TeamsAppInstallation.ReadForTeam | 5248dcb1-f83b-4ec3-9f4d-a4428a961a72 | Admin | Read installed Teams apps in teams |
| TeamsAppInstallation.ReadWriteForChat | aa85bf13-d771-4d5d-a9e6-bca04ce44edf | Admin | Manage installed Teams apps in chats |
| TeamsAppInstallation.ReadWriteForTeam | 2e25a044-2580-450d-8859-42eeb6e996c0 | Admin | Manage installed Teams apps in teams |
| TeamsAppInstallation.ReadWriteForUser | 093f8818-d05f-49b8-95bc-9d2a73e9a43c | Admin | Manage user’s installed Teams apps |
| TeamsAppInstallation.ReadWriteSelfForChat | 0ce33576-30e8-43b7-99e5-62f8569a4002 | Admin | Allow the Teams app to manage itself in chats |
| TeamsAppInstallation.ReadWriteSelfForTeam | 0f4595f7-64b1-4e13-81bc-11a249df07a9 | Admin | Allow the app to manage itself in teams |
| TeamSettings.Read.All | 48638b3c-ad68-4383-8ac4-e6880ee6ca57 | Admin | Read teams’ settings |
| TeamSettings.ReadWrite.All | 39d65650-9d3e-4223-80db-a335590d027e | Admin | Read and change teams’ settings |
| TeamsTab.Create | a9ff19c2-f369-4a95-9a25-ba9d460efc8e | Admin | Create tabs in Microsoft Teams. |
| TeamsTab.Read.All | 59dacb05-e88d-4c13-a684-59f1afc8cc98 | Admin | Read tabs in Microsoft Teams. |
| TeamsTab.ReadWrite.All | b98bfd41-87c6-45cc-b104-e2de4f0dafb9 | Admin | Read and write tabs in Microsoft Teams. |
| TeamsTab.ReadWriteForChat | ee928332-e9c2-4747-b4a0-f8c164b68de6 | Admin | Allow the Teams app to manage all tabs in chats |
| TeamsTab.ReadWriteForTeam | c975dd04-a06e-4fbb-9704-62daad77bb49 | Admin | Allow the Teams app to manage all tabs in teams |
| TeamsTab.ReadWriteSelfForChat | 0c219d04-3abf-47f7-912d-5cca239e90e6 | Admin | Allow the Teams app to manage only its own tabs in chats |
| TeamsTab.ReadWriteSelfForTeam | f266662f-120a-4314-b26a-99b08617c7ef | Admin | Allow the Teams app to manage only its own tabs in teams |
| TeamworkDevice.Read.All | b659488b-9d28-4208-b2be-1c6652b3c970 | Admin | Read Teams devices |
| TeamworkDevice.ReadWrite.All | ddd97ecb-5c31-43db-a235-0ee20e635c40 | Admin | Read and write Teams devices |
| TeamworkTag.Read | 57587d0b-8399-45be-b207-8050cec54575 | Admin | Read tags in Teams |
| TeamworkTag.ReadWrite | 539dabd7-b5b6-4117-b164-d60cd15a8671 | Admin | Read and write tags in Teams |
| TermStore.Read.All | 297f747b-0005-475b-8fef-c890f5152b38 | Admin | Read term store data |
| TermStore.ReadWrite.All | 6c37c71d-f50f-4bff-8fd3-8a41da390140 | Admin | Read and write term store data |
| ThreatAssessment.ReadWrite.All | cac97e40-6730-457d-ad8d-4852fddab7ad | Admin | Read and write threat assessment requests |
| ThreatHunting.Read.All | b152eca8-ea73-4a48-8c98-1a6742673d99 | Admin | Run hunting queries |
| ThreatIndicators.Read.All | 9cc427b4-2004-41c5-aa22-757b755e9796 | Admin | Read all threat indicators |
| ThreatIndicators.ReadWrite.OwnedBy | 91e7d36d-022a-490f-a748-f8e011357b42 | Admin | Manage threat indicators this app creates or owns |
| ThreatSubmission.Read.All | 7083913a-4966-44b6-9886-c5822a5fd910 | Admin | Read all threat submissions |
| ThreatSubmission.ReadWrite.All | 8458e264-4eb9-4922-abe9-768d58f13c7f | Admin | Read and write all threat submissions |
| ThreatSubmissionPolicy.ReadWrite.All | 059e5840-5353-4c68-b1da-666a033fc5e8 | Admin | Read and write all threat submission policies |
| TrustFrameworkKeySet.Read.All | 7ad34336-f5b1-44ce-8682-31d7dfcd9ab9 | Admin | Read trust framework key sets |
| TrustFrameworkKeySet.ReadWrite.All | 39244520-1e7d-4b4a-aee0-57c65826e427 | Admin | Read and write trust framework key sets |
| UnifiedGroupMember.Read.AsGuest | 73e75199-7c3e-41bb-9357-167164dbb415 | Admin | Read unified group memberships as guest |
| User.Export.All | 405a51b5-8d8d-430b-9842-8be4b0e9f324 | Admin | Export user’s data |
| User.Invite.All | 63dd7cd9-b489-4adf-a28c-ac38b9a0f962 | Admin | Invite guest users to the organization |
| User.ManageIdentities.All | 637d7bec-b31e-4deb-acc9-24275642a2c9 | Admin | Manage user identities |
| User.Read.All | a154be20-db9c-4678-8ab7-66f6cc099a59 | Admin | Read all users’ full profiles |
| User.ReadWrite.All | 204e0828-b5ca-4ad8-b9f3-f32a958e7cc4 | Admin | Read and write all users’ full profiles |
| UserAuthenticationMethod.Read | 1f6b61c5-2f65-4135-9c9f-31c0f8d32b52 | Admin | Read user authentication methods. |
| UserAuthenticationMethod.Read.All | aec28ec7-4d02-4e8c-b864-50163aea77eb | Admin | Read all users’ authentication methods |
| UserAuthenticationMethod.ReadWrite | 48971fc1-70d7-4245-af77-0beb29b53ee2 | Admin | Read and write user authentication methods |
| UserAuthenticationMethod.ReadWrite.All | b7887744-6746-4312-813d-72daeaee7e2d | Admin | Read and write all users’ authentication methods. |
| WindowsUpdates.ReadWrite.All | 11776c0c-6138-4db3-a668-ee621bea2555 | Admin | Read and write all Windows update deployment settings |
| WorkforceIntegration.Read.All | f1ccd5a7-6383-466a-8db8-1a656f7d06fa | Admin | Read workforce integrations |
| WorkforceIntegration.ReadWrite.All | 08c4b377-0d23-4a8b-be2a-23c1c1d88545 | Admin | Read and write workforce integrations |
| Analytics.Read | e03cf23f-8056-446a-8994-7d93dfc8b50e | User | Read your activity statistics |
| AppCatalog.Read.All | 88e58d74-d3df-44f3-ad47-e89edf4472e4 | User | Read all app catalogs |
| AppCatalog.Submit | 3db89e36-7fa6-4012-b281-85f3d9d9fd2e | User | Submit application packages to your organization’s catalog and cancel pending submissions |
| Bookings.Manage.All | 7f36b48e-542f-4d3b-9bcb-8406f0ab9fdb | User | Manage bookings information |
| Bookings.Read.All | 33b1df99-4b29-4548-9339-7a7b83eaeebc | User | Read bookings information |
| Bookings.ReadWrite.All | 948eb538-f19d-4ec5-9ccc-f059e1ea4c72 | User | Read and write bookings information |
| BookingsAppointment.ReadWrite.All | 02a5a114-36a6-46ff-a102-954d89d9ab02 | User | Read and write booking appointments |
| Calendars.Read | 465a38f9-76ea-45b9-9f34-9e8b0d4b0b42 | User | Read your calendars |
| Calendars.Read.Shared | 2b9c4092-424d-4249-948d-b43879977640 | User | Read calendarsyou can access |
| Calendars.ReadWrite | 1ec239c2-d7c9-4623-a91a-a9775856bb36 | User | Have full access to your calendars |
| Calendars.ReadWrite.Shared | 12466101-c9b8-439a-8589-dd09ee67e8e9 | User | Read and write to your and shared calendars |
| Channel.ReadBasic.All | 9d8982ae-4365-4f57-95e9-d6032a4c0b87 | User | Read the names and descriptions of channels |
| ChannelMessage.Edit | 2b61aa8a-6d36-4b2f-ac7b-f29867937c53 | User | Edit your channel messages |
| ChannelMessage.Send | ebf0f66e-9fb1-49e4-a278-222f76911cf4 | User | Send channel messages |
| Chat.Create | 38826093-1258-4dea-98f0-00003be2b8d0 | User | Create chats |
| Chat.Read | f501c180-9344-439a-bca0-6cbf209fd270 | User | Read your chat messages |
| Chat.ReadBasic | 9547fcb5-d03f-419d-9948-5928bbf71b0f | User | Read names and members of your chat threads |
| Chat.ReadWrite | 9ff7295e-131b-4d94-90e1-69fde507ac11 | User | Read and write your chat messages |
| ChatMessage.Read | cdcdac3a-fd45-410d-83ef-554db620e5c7 | User | Read user chat messages |
| ChatMessage.Send | 116b7235-7cc6-461e-b163-8e55691d839e | User | Send chat messages |
| CloudPC.Read.All | 5252ec4e-fd40-4d92-8c68-89dd1d3c6110 | User | Read Cloud PCs |
| Contacts.Read | ff74d97f-43af-4b68-9f2a-b77ee6968c5d | User | Read your contacts |
| Contacts.Read.Shared | 242b9d9e-ed24-4d09-9a52-f43769beb9d4 | User | Read your and shared contacts |
| Contacts.ReadWrite | d56682ec-c09e-4743-aaf4-1a3aac4caa21 | User | Have full access of your contacts |
| Contacts.ReadWrite.Shared | afb6c84b-06be-49af-80bb-8f3f77004eab | User | Read and write to your and shared contacts |
| Device.Command | bac3b9c2-b516-4ef4-bd3b-c2ef73d8d804 | User | Communicate with your other devices |
| Device.Read | 11d4cd79-5ba5-460f-803f-e22c8ab85ccd | User | View your list of devices |
| EAS.AccessAsUser.All | ff91d191-45a0-43fd-b837-bd682c4a0b0f | User | Access your mailboxes |
| email | 64a6cdd6-aab1-4aaf-94b8-3cc8405e90d0 | User | View your email address |
| EWS.AccessAsUser.All | 9769c687-087d-48ac-9cb3-c37dde652038 | User | Access your mailboxes |
| Family.Read | 3a1e4806-a744-4c70-80fc-223bf8582c46 | User | Read your family info |
| Files.Read | 10465720-29dd-4523-a11a-6a75c743c9d9 | User | Read your files |
| Files.Read.All | df85f4d6-205c-4ac5-a5ea-6bf408dba283 | User | Read all files that you have access to |
| Files.Read.Selected | 5447fe39-cb82-4c1a-b977-520e67e724eb | User | Read selected files |
| Files.ReadWrite | 5c28f0bf-8a70-41f1-8ab2-9032436ddb65 | User | Have full access to your files |
| Files.ReadWrite.All | 863451e7-0667-486c-a5d6-d135439485f0 | User | Have full access to all files you have access to |
| Files.ReadWrite.AppFolder | 8019c312-3263-48e6-825e-2b833497195b | User | Have full access to the application’s folder |
| Files.ReadWrite.Selected | 17dde5bd-8c17-420f-a486-969730c1b827 | User | Read and write selected files |
| Financials.ReadWrite.All | f534bf13-55d4-45a9-8f3c-c92fe64d6131 | User | Read and write financials data |
| IMAP.AccessAsUser.All | 652390e4-393a-48de-9484-05f9b1212954 | User | Read and write access to your mail. |
| InformationProtectionPolicy.Read | 4ad84827-5578-4e18-ad7a-86530b12f884 | User | Read user sensitivity labels and label policies. |
| Mail.Read | 570282fd-fa5c-430d-a7fd-fc8dc98a9dca | User | Read your mail |
| Mail.Read.Shared | 7b9103a5-4610-446b-9670-80643382c1fa | User | Read mail you can access |
| Mail.ReadBasic | a4b8392a-d8d1-4954-a029-8e668a39a170 | User | Read user basic mail |
| Mail.ReadWrite | 024d486e-b451-40bb-833d-3e66d98c5c73 | User | Read and write access to your mail |
| Mail.ReadWrite.Shared | 5df07973-7d5d-46ed-9847-1271055cbd51 | User | Read and write mailyou can access |
| Mail.Send | e383f46e-2787-4529-855e-0e479a3ffac0 | User | Send mail as you |
| Mail.Send.Shared | a367ab51-6b49-43bf-a716-a1fb06d2a174 | User | Send mail on behalf of others or yourself |
| MailboxSettings.Read | 87f447af-9fa4-4c32-9dfa-4a57a73d18ce | User | Read your mailbox settings |
| MailboxSettings.ReadWrite | 818c620a-27a9-40bd-a6a5-d96f7d610b4b | User | Read and write to your mailbox settings |
| Notes.Create | 9d822255-d64d-4b7a-afdb-833b9a97ed02 | User | Create your OneNote notebooks |
| Notes.Read | 371361e4-b9e2-4a3f-8315-2a301a3b0a3d | User | Read your OneNote notebooks |
| Notes.Read.All | dfabfca6-ee36-4db2-8208-7a28381419b3 | User | Read all OneNote notebooks that you can access |
| Notes.ReadWrite | 615e26af-c38a-4150-ae3e-c3b0d4cb1d6a | User | Read and write your OneNote notebooks |
| Notes.ReadWrite.All | 64ac0503-b4fa-45d9-b544-71a463f05da0 | User | Read and write all OneNote notebooks that you can access |
| Notes.ReadWrite.CreatedByApp | ed68249d-017c-4df5-9113-e684c7f8760b | User | Limited access to your OneNote notebooks for this app (preview) |
| Notifications.ReadWrite.CreatedByApp | 89497502-6e42-46a2-8cb2-427fd3df970a | User | Deliver and manage your notifications for this app |
| offline_access | 7427e0e9-2fba-42fe-b0c0-848c9e6a8182 | User | Maintain access to data you have given it access to |
| OnlineMeetingArtifact.Read.All | 110e5abb-a10c-4b59-8b55-9b4daa4ef743 | User | Read user’s online meeting artifacts |
| OnlineMeetings.Read | 9be106e1-f4e3-4df5-bdff-e4bc531cbe43 | User | Read your online meetings |
| OnlineMeetings.ReadWrite | a65f2972-a4f8-4f5e-afd7-69ccb046d5dc | User | Read and create your online meetings |
| openid | 37f7f235-527c-4136-accd-4a02d197296e | User | Sign in as you |
| People.Read | ba47897c-39ec-4d83-8086-ee8256fa737d | User | Read your relevant people list |
| Policy.Read.ConditionalAccess | 633e0fce-8c58-4cfb-9495-12bbd5a24f7c | User | Read your organization’s conditional access policies |
| POP.AccessAsUser.All | d7b7f2d9-0f45-4ea1-9d42-e50810c06991 | User | Read and write access to your mail. |
| Presence.Read | 76bc735e-aecd-4a1d-8b4c-2b915deabb79 | User | Read your presence information |
| Presence.Read.All | 9c7a330d-35b3-4aa1-963d-cb2b9f927841 | User | Read presence information of all users in your organization |
| Presence.ReadWrite | 8d3c54a7-cf58-4773-bf81-c0cd6ad522bb | User | Read and write your presence information |
| PrinterShare.Read.All | ed11134d-2f3f-440d-a2e1-411efada2502 | User | Read printer shares |
| PrinterShare.ReadBasic.All | 5fa075e9-b951-4165-947b-c63396ff0a37 | User | Read basic information about printer shares |
| PrintJob.Create | 21f0d9c0-9f13-48b3-94e0-b6b231c7d320 | User | Create your print jobs |
| PrintJob.Read | 248f5528-65c0-4c88-8326-876c7236df5e | User | Read your print jobs |
| PrintJob.ReadBasic | 6a71a747-280f-4670-9ca0-a9cbf882b274 | User | Read basic information of your print jobs |
| PrintJob.ReadWrite | b81dd597-8abb-4b3f-a07a-820b0316ed04 | User | Read and update your print jobs |
| PrintJob.ReadWriteBasic | 6f2d22f2-1cb6-412c-a17c-3336817eaa82 | User | Read and write basic information of your print jobs |
| profile | 14dad69e-099b-42c9-810b-d002981feec1 | User | View your basic profile |
| ShortNotes.Read | 50f66e47-eb56-45b7-aaa2-75057d9afe08 | User | Read your short notes |
| ShortNotes.ReadWrite | 328438b7-4c01-4c07-a840-e625a749bb89 | User | Read, create, edit, and delete your short notes |
| Sites.Manage.All | 65e50fdc-43b7-4915-933e-e8138f11f40a | User | Create, edit, and delete items and lists in all your site collections |
| Sites.Read.All | 205e70e5-aba6-4c52-a976-6d2d46c48043 | User | Read items in all site collections |
| Sites.ReadWrite.All | 89fe6a52-be36-487e-b7d8-d061c450a026 | User | Edit or delete items in all site collections |
| SMTP.Send | 258f6531-6087-4cc4-bb90-092c5fb3ed3f | User | Access to sending emails from your mailbox. |
| Tasks.Read | f45671fb-e0fe-4b4b-be20-3d3ce43f1bcb | User | Read your tasks and task lists |
| Tasks.Read.Shared | 88d21fd4-8e5a-4c32-b5e2-4a1c95f34f72 | User | Read your and shared tasks |
| Tasks.ReadWrite | 2219042f-cab5-40cc-b0d2-16b1540b4c5f | User | Create, read, update, and delete your tasks and task lists |
| Tasks.ReadWrite.Shared | c5ddf11b-c114-4886-8558-8a4e557cd52b | User | Read and write to your and shared tasks |
| Team.Create | 7825d5d6-6049-4ce7-bdf6-3b8d53f4bcd0 | User | Create teams |
| Team.ReadBasic.All | 485be79e-c497-4b35-9400-0e3fa7f2a5d4 | User | Read the names and descriptions of teams |
| TeamsActivity.Read | 0e755559-83fb-4b44-91d0-4cc721b9323e | User | Read your teamwork activity feed |
| TeamsActivity.Send | 7ab1d787-bae7-4d5d-8db6-37ea32df9186 | User | Send a teamwork activity |
| TeamsAppInstallation.ReadForChat | bf3fbf03-f35f-4e93-963e-47e4d874c37a | User | Read installed Teams apps in chats |
| TeamsAppInstallation.ReadForUser | c395395c-ff9a-4dba-bc1f-8372ba9dca84 | User | Read your installed Teams apps |
| TeamsAppInstallation.ReadWriteSelfForUser | 207e0cb1-3ce7-4922-b991-5a760c346ebc | User | Allow the Teams app to manage itself for you |
| TeamsTab.ReadWriteForUser | c37c9b61-7762-4bff-a156-afc0005847a0 | User | Allow the Teams app to manage all tabs for you |
| TeamsTab.ReadWriteSelfForUser | 395dfec1-a0b9-465f-a783-8250a430cb8c | User | Allow the Teams app to manage only its own tabs for you |
| ThreatSubmission.Read | fd5353c6-26dd-449f-a565-c4e16b9fce78 | User | Read threat submissions |
| ThreatSubmission.ReadWrite | 68a3156e-46c9-443c-b85c-921397f082b5 | User | Read and write threat submissions |
| User.Read | e1fe6dd8-ba31-4d61-89e7-88639da4683d | User | Sign you in and read your profile |
| User.ReadBasic.All | b340eb25-3456-403f-be2f-af7a0d370277 | User | Read all users’ basic profiles |
| User.ReadWrite | b4e74841-8e56-480b-be8b-910348b18b4c | User | Read and update your profile |
| UserActivity.ReadWrite.CreatedByApp | 47607519-5fb1-47d9-99c7-da4b48f369b1 | User | Read and write app activity to your activity feed |
| UserNotification.ReadWrite.CreatedByApp | 26e2f3e8-b2a1-47fc-9620-89bb5b042024 | User | Deliver and manage your notifications |
| UserTimelineActivity.Write.CreatedByApp | 367492fc-594d-4972-a9b5-0d58c622c91c | User | Write app activity to your timeline |