Many organizations implement MFA as a common requirement for security and to address identity theft. Legacy authentication doesn’t support MFA. Blocking legacy authentication will improve your tenant’s protection.
I have detailed on how to disable protocols using basic authentication using authentication policies in a different post here. I’ll go into detail on how to block legacy authentication using Azure AD Conditional Access.
Remember: Conditional Access policies take effect after the first-factor authentication is completed. In a scenario where a user's credentials were leaked, then attackers use it to gain access but signal generated from these events like location of the request, sign-in risk level can be used to block access.
Clients using legacy authentication cannot enforce MFA. Examples of such applications,
- Microsoft Office 2013 or older
- Apps using mail protocols like IMAP, POP
Block legacy authentication
There are two ways Conditional Access policies can be used to block legacy authentication,
- Direct Method
- Indirect Method
Direct Method
- In Azure AD admin center, click on the Security tab(https://aad.portal.azure.com/)
- Click Conditional Access and Create a new policy
I typically prefix Conditional Access policies with ‘Grant Access’ or ‘Block Access’ in the tenants I manage.
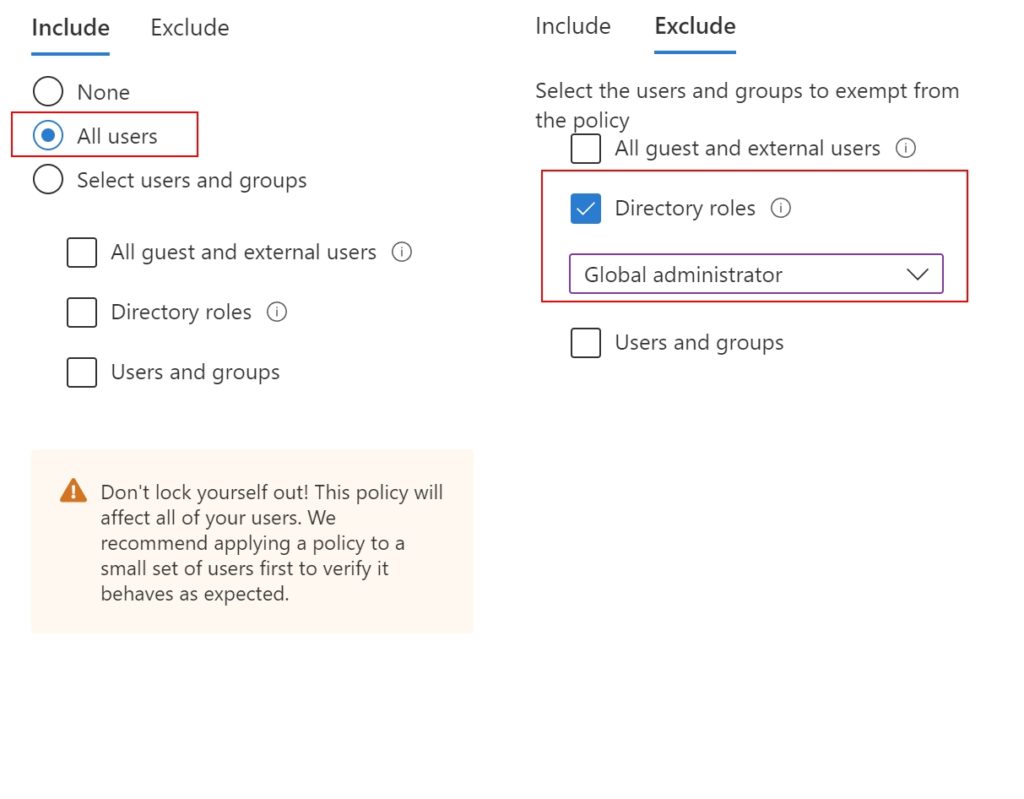
Under Users
- Include : ‘All users’
- I’ll exclude ‘Global administrator’ role just to be on the safe side of things
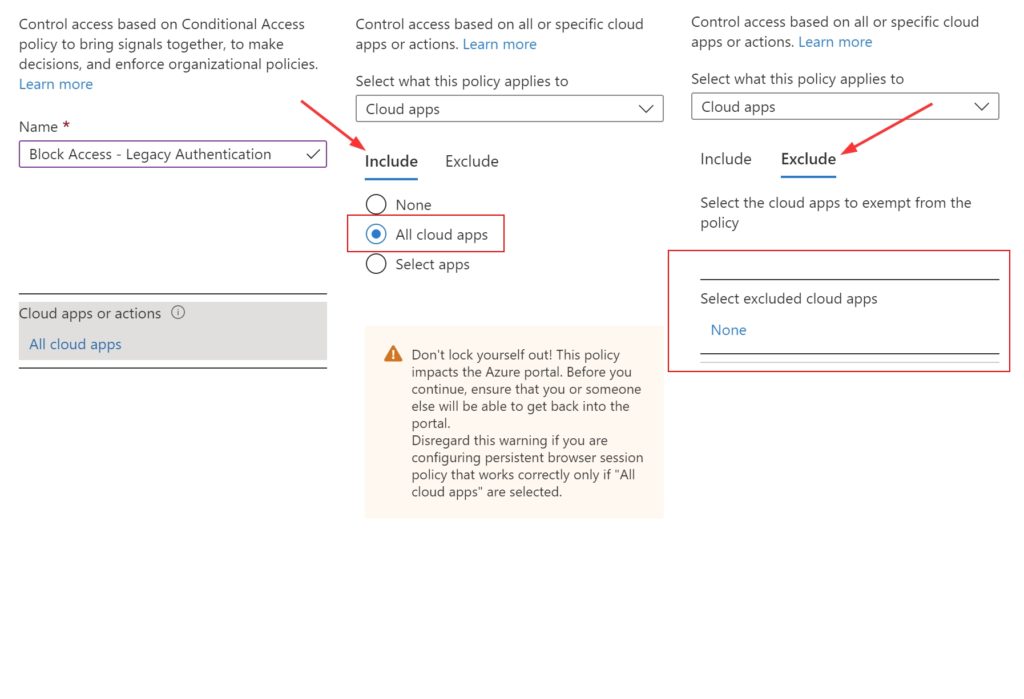
Under ‘Cloud apps or actions‘
- Include : All cloud apps
- Exclude : None
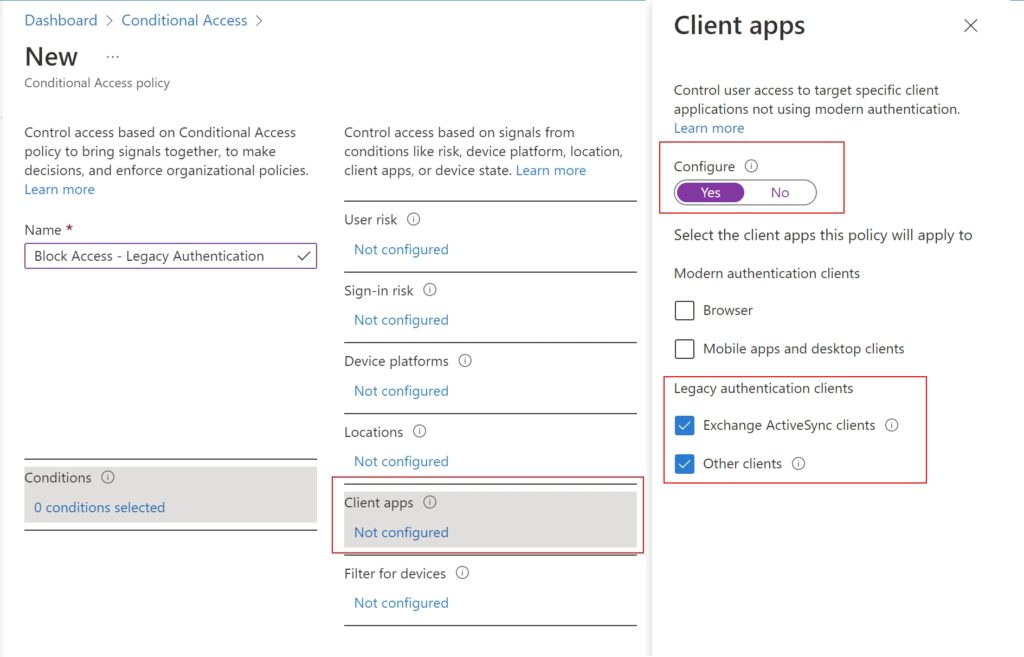
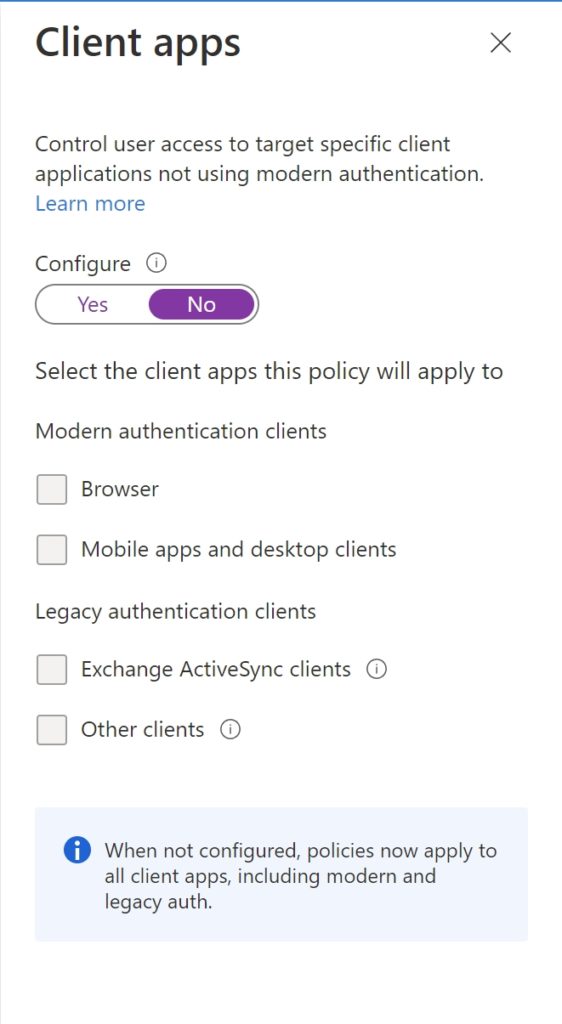
In Conditions –> Client Apps,
- Select ‘Yes‘ to configure policy
- Uncheck ‘Browser‘ and ‘Mobile apps and desktop clients‘ which are checked by default
- ‘Exchange ActiveSync clients‘ and ‘Other clients‘ needs to be left checked
- Click ‘Done‘
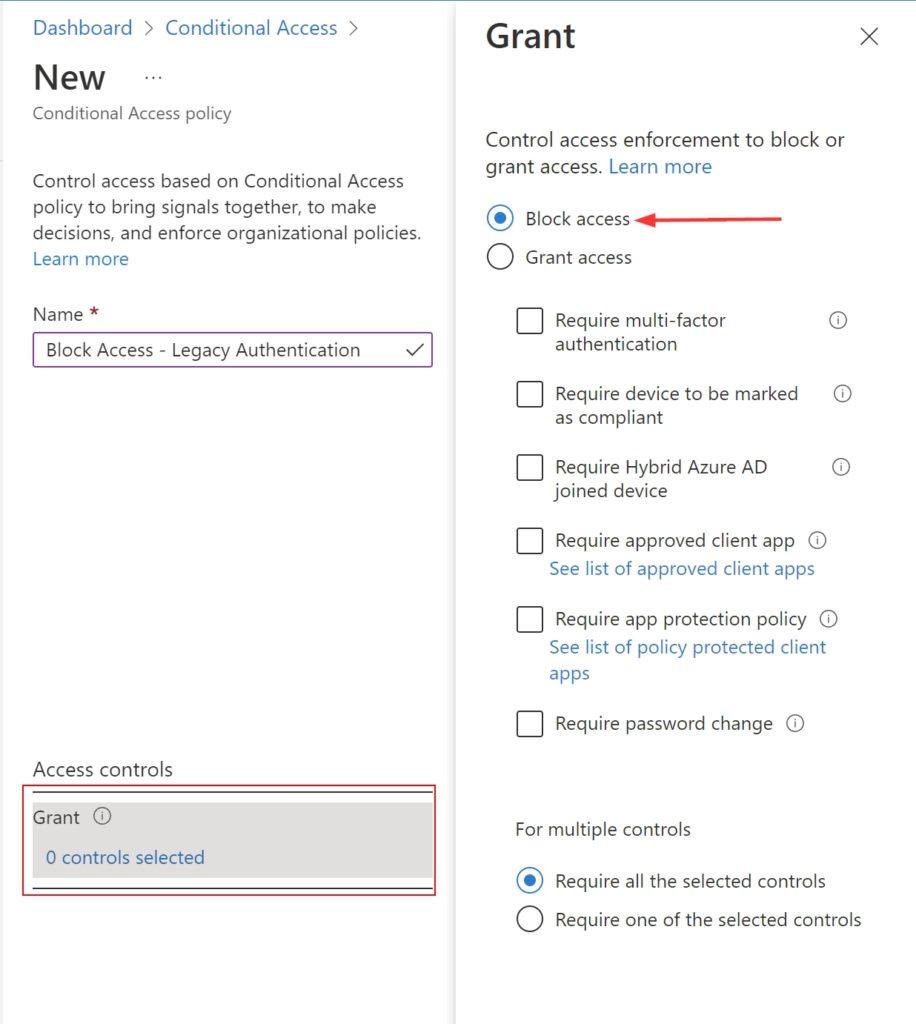
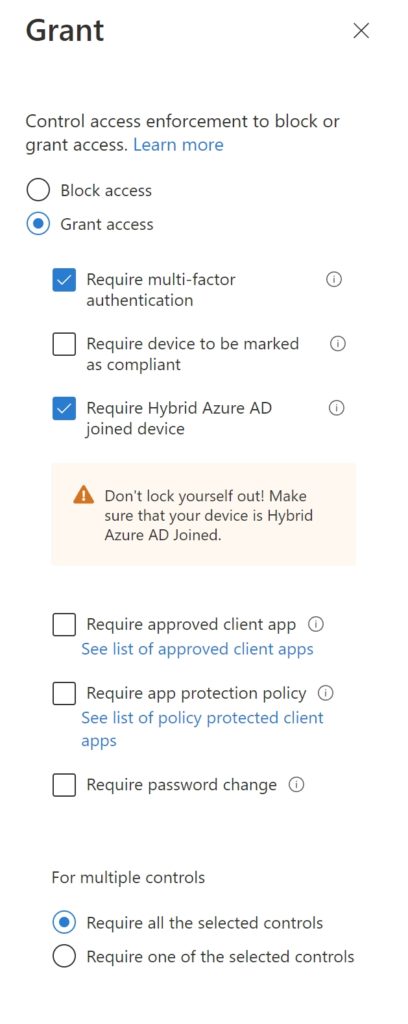
Grant: Select ‘Block access‘
While taking this approach, it is better to set the policy to ‘Report Only‘. This way, you can get some insights on what is using legacy authentication and hopefully you won’t break business critical applications in a production environment. Or if you like living life on the edge, go for it and set it to ‘On‘
Indirect Method
In this method, the policy creation steps are same as the ‘Direct method’.
- When it comes to choosing the ‘Client apps‘, Configure ‘No‘
- In ‘Grant‘, select ‘Grant Access‘ and ‘Require multi-factor authentication‘ and ‘Require Hybrid Azure AD joined device‘
During authentication, legacy authentication clients don’t support sending MFA, Azure AD join state or device compliance. When we apply policies with grant controls to all client applications, the legacy authentication based sign-ins that cannot satisfy these required grant controls are blocked.
Conditional Access policies can take up 24 hours to take effect. Please keep this in mind while rolling out changes in a production environment. What seems to be working immediately after you put the policy in place might not work when you wake up the next day as the policy is just taking effect or even worse while you are on a camping weekend with no cell coverage..Live and learn.. I guess.😁
Thank you for stopping by. ✌