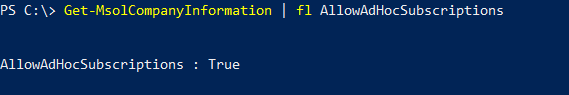
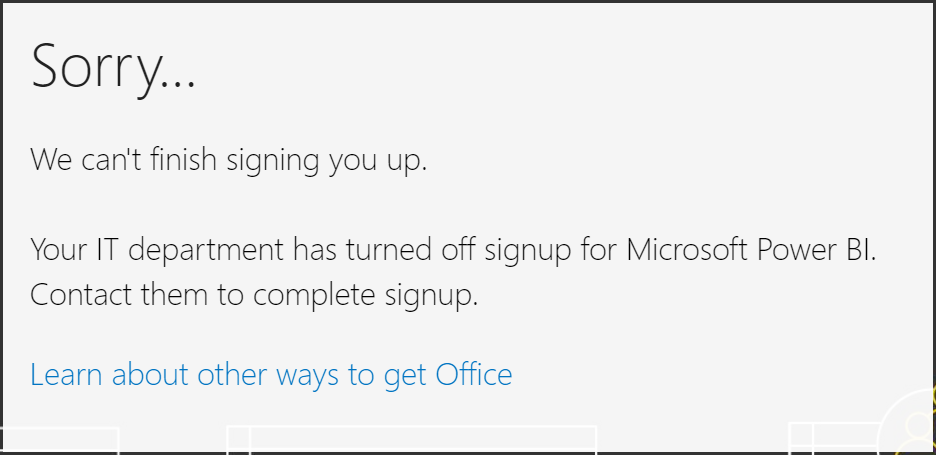
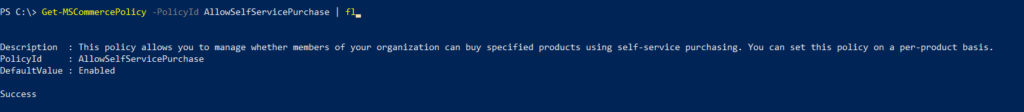
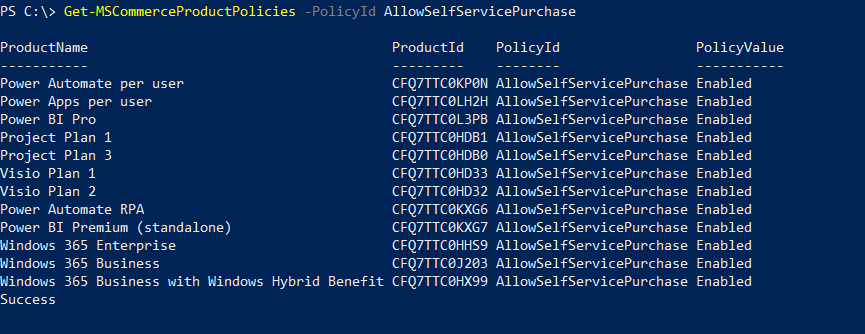
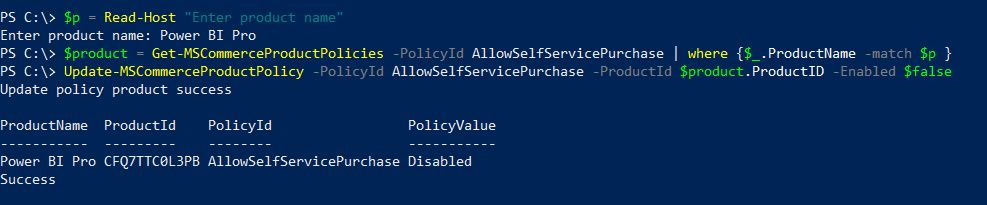
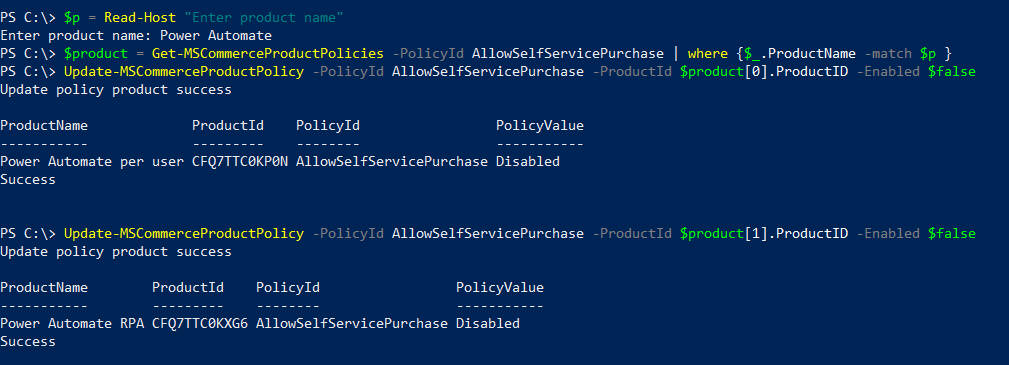
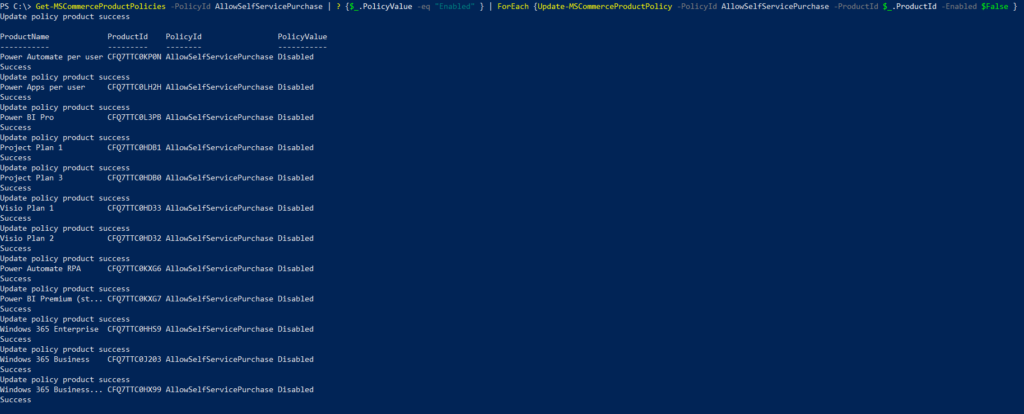
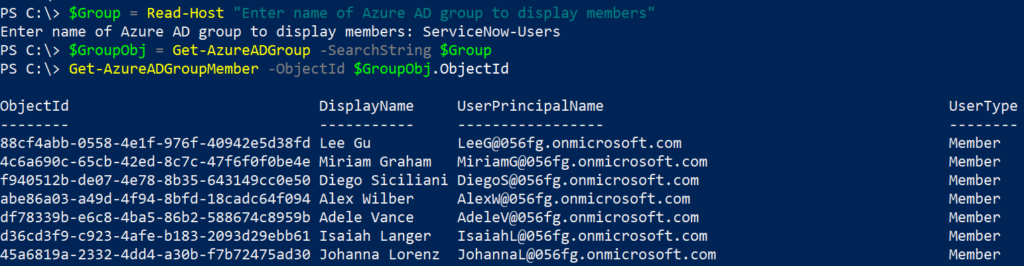
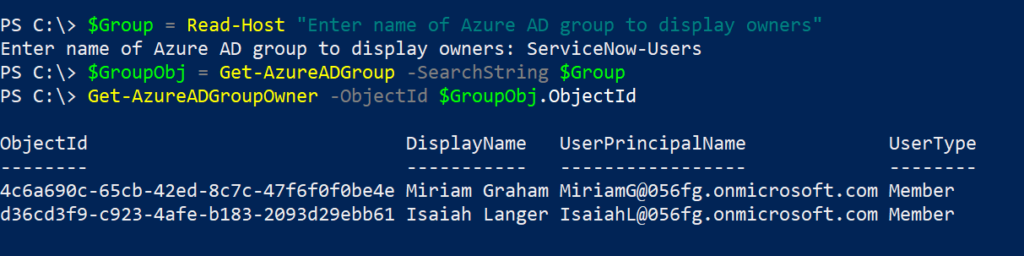
In this post, I’ll go through the steps to create distribution groups in O365 using PowerShell.
Before proceeding further make sure you are connected to Exchange Online,
$o365cred = Get-Credential
Connect-ExchangeOnline -credential $o365credTo create a mail-enabled security group named Managers without specifying any members:
$Name = Read-Host "Enter a name for the DistributionGroup"
New-DistributionGroup -Type "Security" -Name $Name -DisplayName $Name -Alias $Name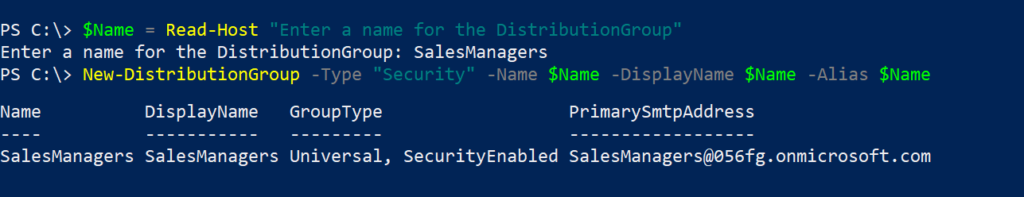
To create a mail-enabled security group named Managers with members:
Note: -Member is a ‘MultiValuedProperty’ and as we input users comma seperated, we need to split the (comma-separated) string to get an actual array.
$Name = Read-Host "Enter a name for the DistributionGroup"
$Members = Read-Host "Enter email addresses seperated by comma"
$members = $members -split ' *, *'
New-DistributionGroup -Type "Security" -Name $Name -DisplayName $Name -Alias $Name -Members $Members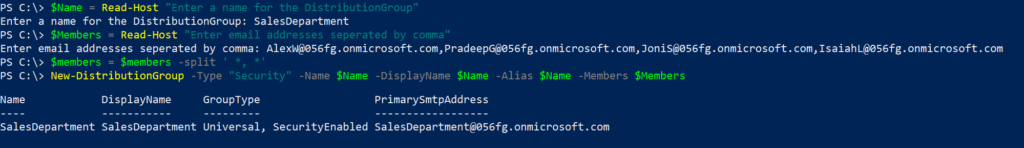
To add multiple members to an existing Distribution Group:
$Name = Read-Host "Enter DistributionGroup name to add members"
$Members = "user01@domain.onmicrosoft.com","user01@domain.onmicrosoft.com"
$Members | ForEach-Object { Add-DistributionGroupMember -Identity $Name -Member $_}To import members from a csv and add to an existing Distribution Group:
$Name = Read-Host "Enter DistributionGroup name to add members"
Import-csv "C:\tmp\members.csv" | ForEach-Object {
Add-DistributionGroupMember -Identity $Name -Member $_.member
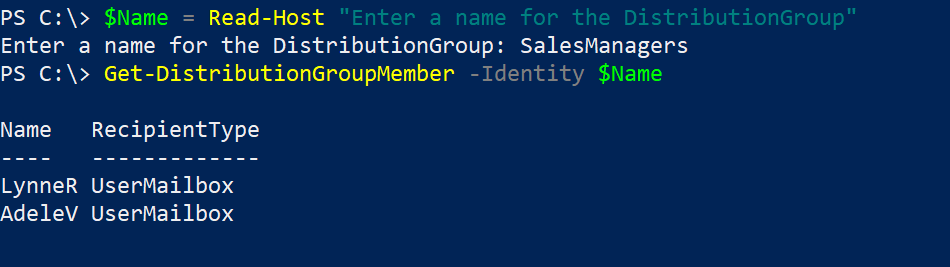
}To determine existing distribution group members for a distribution group:
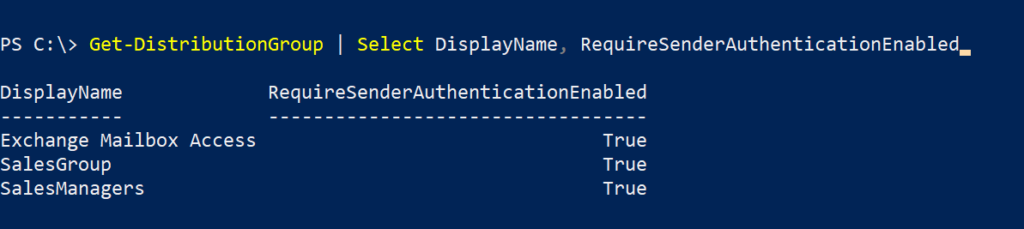
To set distribution group to accept messages from authenticated (internal) and unauthenticated (external) senders.
Note: If you don’t specify this parameter while creating the distribution group, the default value is set to ‘true’ meaning messages from unauthenticated (external) senders are rejected.
$Name = Read-Host "Enter DistributionGroup's name to allow external senders"
Set-DistributionGroup -Identity $Name -RequireSenderAuthenticationEnabled $false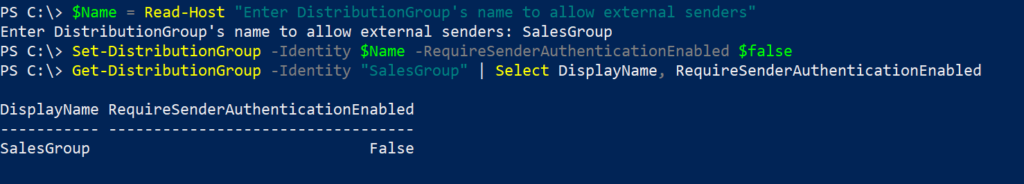
To change an existing distribution group’s name:
$Name = Read-Host "Enter name of existing group to be renamed"
$NewName = Read-Host "Enter new name"
Set-DistributionGroup -Identity $Name -Name $NewName -DisplayName $NewName -Alias $NewNameThank you for stopping by. ✌