Microsoft recently announced they will disable basic authentication for all M365 tenants. This deadline has been pushed postponed due to the impact of COVID-19 across the globe.
Latest update: The latest from Microsoft is, effective October 1, 2022 Basic authentication will be disabled in all tenants.
The following components of Exchange Online will be affected,
- Exchange Web Services(EWS)
- POP
- IMAP
- Exchange ActiveSync
- Remote PowerShell
Table of Contents
Why is this a big deal?
Basic authentication uses username and password for client access requests. This used to be the industry standard during the time which organizations didn’t understand the cost of security breaches. It poses a significant security risk as Business Email Compromise (BEC) scams have exposed organizations to billions of dollars in potential losses. Check out this 2019 report from ProofPoint that goes into details.
Disabling Basic Authentication will help protect Exchange Online from brute force or password spray attacks. As the above mentioned report goes into, IMAP-based password-spraying campaigns are very effective in particular.
Beyond all this, Basic Authentication doesn’t enforce MFA and this should be the biggest driver for organizations to move away from it.
Is Basic Authentication enabled in your tenant?
Here is how to check if Basic Authentication is enabled in your tenant,
- Login to the O365 admin portal (https://admin.microsoft.com/)
- Settings –> Org Settings –> Services –> Modern Authentication
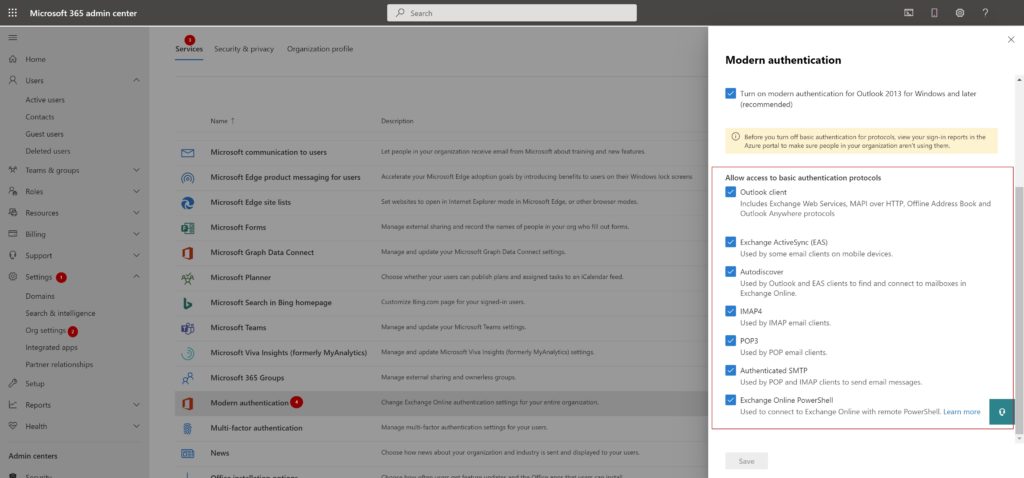
Determine who is using Basic Authentication in your tenant
Before you turn off basic authentication for protocols, view your sign-in reports in the Azure AD portal to determine who is using it in your organization.
This can be determined using sign-in logs in Azure AD.
In your Azure AD admin center, Click the ‘Sign-in logs’ blade.,
- Select ‘Last 1 month‘ in the Date
- Add a ‘Client app‘ as a second filter, choose all options under the ‘Legacy Authentication Clients‘ and click ‘Apply‘
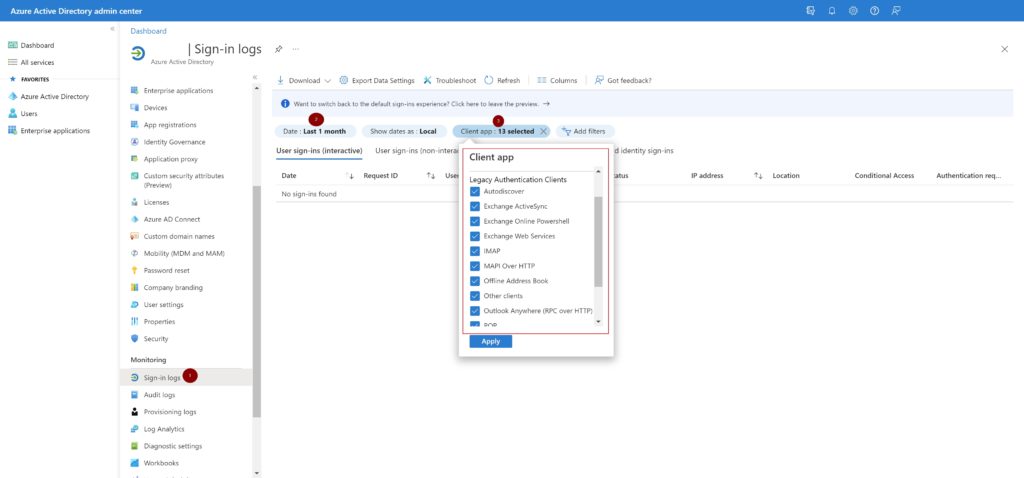
With this report information, you can contact the application and account owners to determine why Basic Authentication is still in use. This information will also come in handy later if you are planning to allow exceptions to these accounts/applications. I’ve covered it later in this post.
Disable Basic Authentication
Before you begin,
- Verify Modern Authentication is enabled
- Verify your email clients are Modern Authentication capable
In this post, I’ve elaborated how to block Basic Authentication using Azure AD conditional access.
IMO, the easiest method to disable Basic Authentication is to use authentication policies.
With Authentication policies you can,
- Apply a default organization level policy that blocks Basic Authentication
- Apply a per user policy to allow certain protocols. Example: ActiveSync
Create Authentication Policy
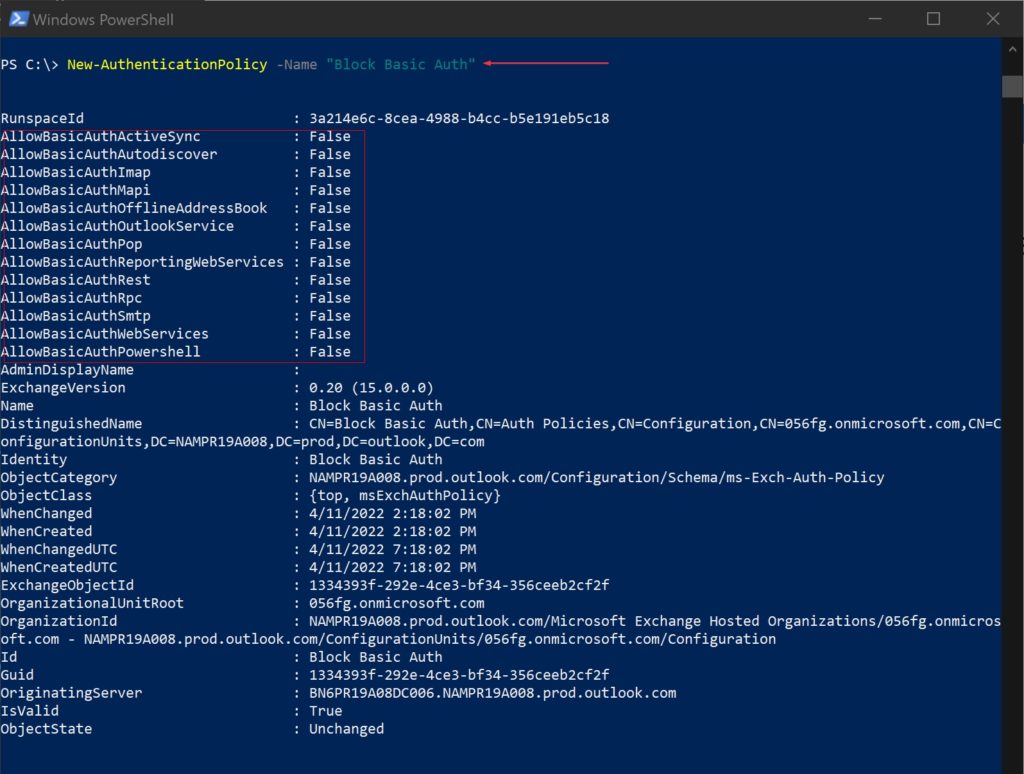
This creates an authentication policy named ‘Block Basic Auth’
New-AuthenticationPolicy -Name "Block Basic Auth"When you create a new authentication policy without specifying any protocols, Basic Authentication is blocked for all client protocols in Exchange Online.
Set Default Authentication Policy
The default policy is assigned to all users in the tenant who don’t have a specific policy assigned to them. To configure the default authentication policy for the organization, use this:
Set-OrganizationConfig -DefaultAuthenticationPolicy "Block Basic Auth"To verify that a default authentication policy is configured,
Get-OrganizationConfig | Format-Table DefaultAuthenticationPolicy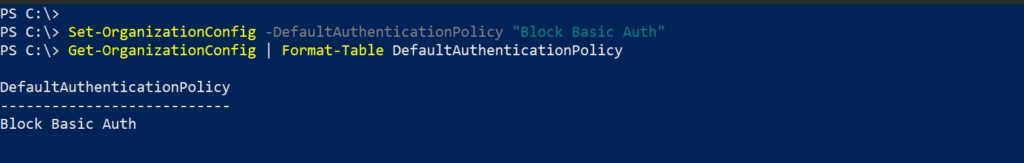
Create user specific authentication policies
Authentication policies assigned to users take precedence over the default organization policy.
- To enable Basic authentication for a specific protocol that’s disabled, specify the switch without a value
- To disable Basic authentication for a specific protocol that’s enabled, use the value :$false
In this scenario, I’m creating an authentication policy to allow ActiveSync. This is sometimes typical in organizations where users will have Intune managed devices but would like to add second O365 email from a different tenant. The Outlook app prevents this but the built-in mail app can be used with ActiveSync to fetch email.
New-AuthenticationPolicy -Name "Allow ActiveSync" -AllowBasicAuthActiveSync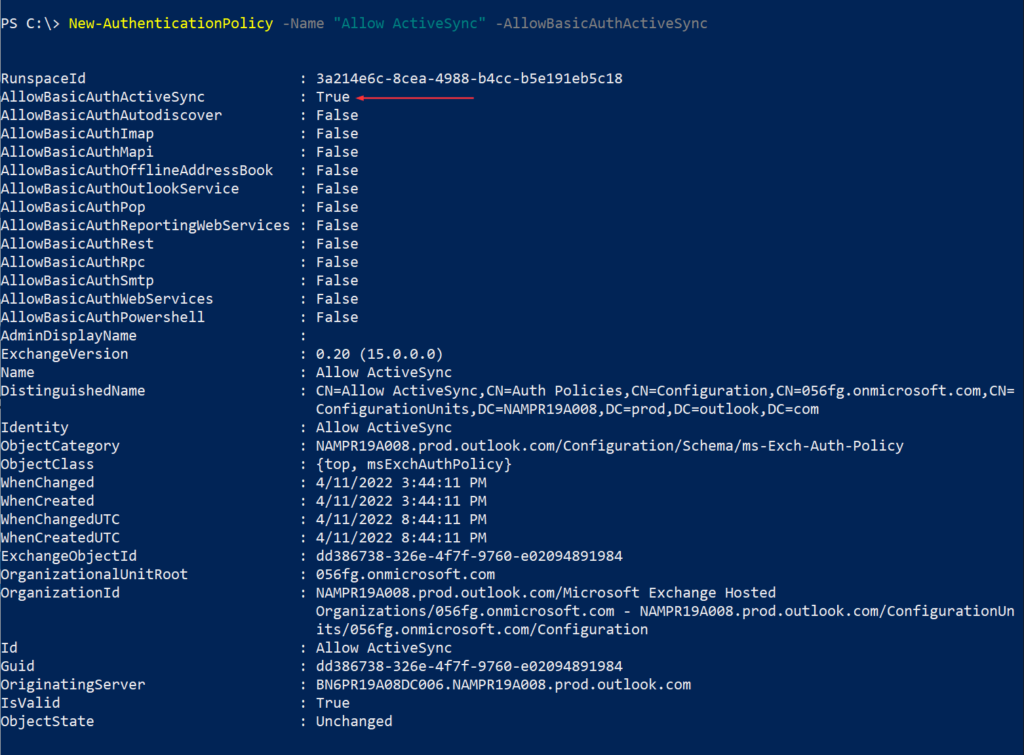
This example assigns the policy named ‘Allow ActiveSync’ to the user account ‘JoniS’
$Id = Read-Host "Enter user's email address"
Set-User -Identity $Id -AuthenticationPolicy "Allow ActiveSync"To confirm the policy is assigned,
Get-User -Identity $Id | fl AuthenticationPolicy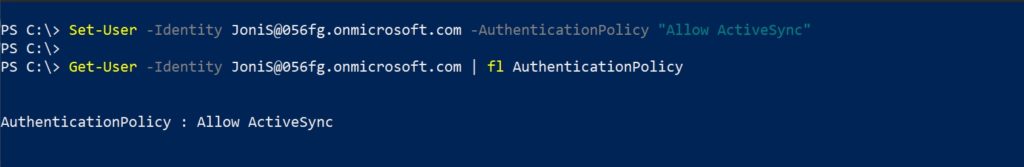
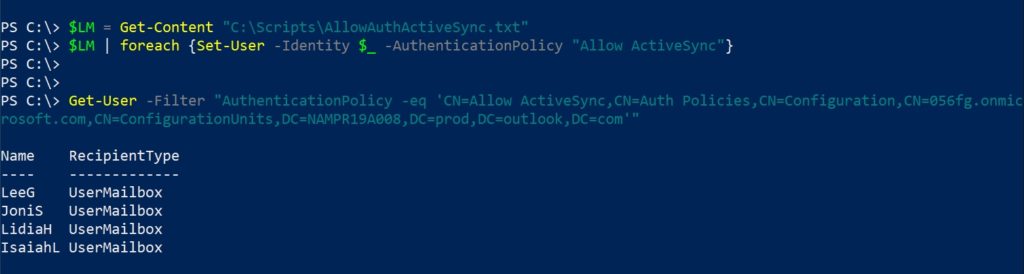
To assign a policy to a list of users, fill text file with the user’s UPN one per line.,
$LM = Get-Content "C:\Scripts\AllowAuthActiveSync.txt"
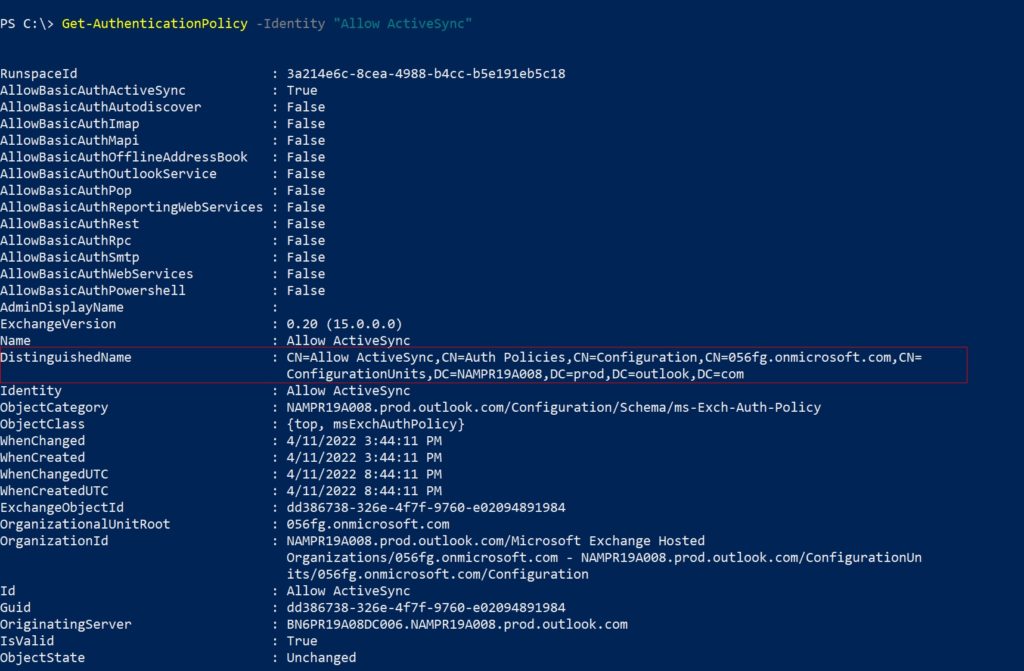
$LM | foreach {Set-User -Identity $_ -AuthenticationPolicy "Allow ActiveSync"}To get all users assigned to a policy you need to get the policy’s DN using the cmdlet Get-AuthenticationPolicy,
$PolicyId = Read-Host "Enter policy ID in distinguished name format"
Get-User -Filter "AuthenticationPolicy -eq '$PolicyId'"
By default, when you create or change the authentication policy assignment on users or update the policy, the changes take effect within 24 hours. If you want the policy to take effect within 30 minutes, use the following syntax:
$Id = Read-Host "Enter user's email address"
Set-User -Identity $Id -STSRefreshTokensValidFrom $([System.DateTime]::UtcNow)This example below immediately applies the authentication policy to multiple users. As I’m in the same PowerShell session and haven’t changed the variables you used to identify the users,
$LM | foreach {Set-User -Identity $_ -STSRefreshTokensValidFrom $([System.DateTime]::UtcNow)}Depending on your organizational requirement, you can create additional authentication policies allowing other protocols and assigning it to users.
And it’s highly recommended to keep track of these users and eventually remove these exceptions.
Thank you for stopping by. ✌