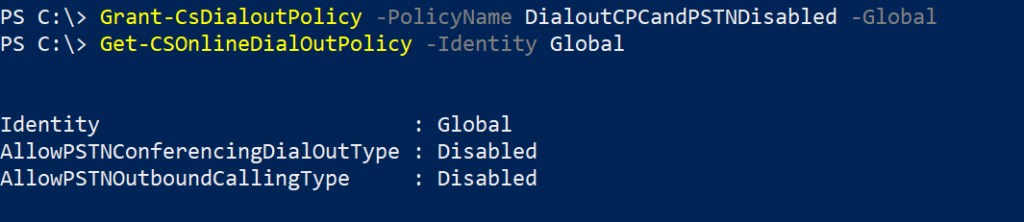
It is important to know about the current state of your Teams rollout and this is one of those which can easily get out of control in a blink of an eye. I wanted to understand and determine the current Teams state in a tenant I manage and I had to create reports to present.
The portal does give a few options to export the data but I decided to take a look at the option the Teams PowerShell module offers. I spent some time on creating a script that will output these five reports,
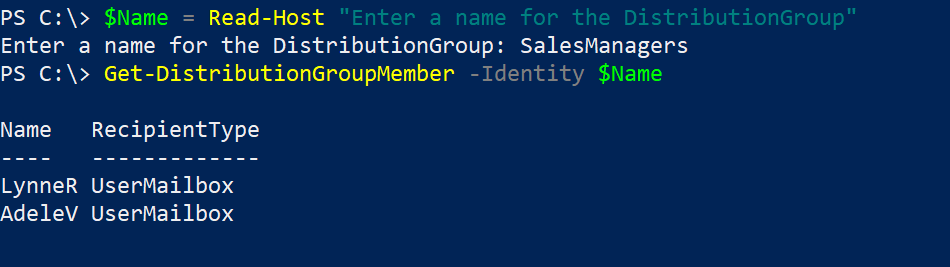
- All Teams data with Channel type, Channel count, Channel count with types, Teams member count and owners count
- Teams users data with role information
- Channel information for each Teams with Channel types
- Channel user information with user information and role
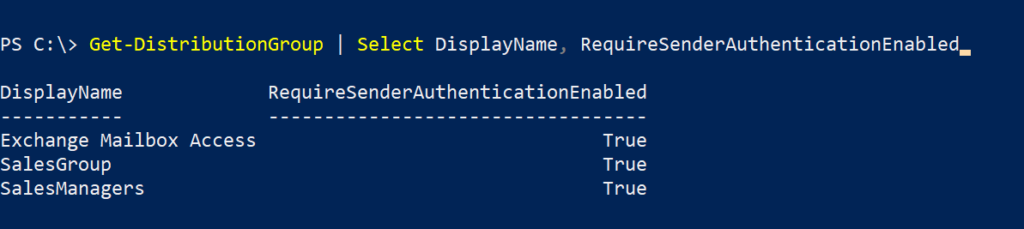
- Permissions on each Teams
This report can also be scheduled to run if you already use a mechanism to store your credentials securely and pass it on to your PS scripts.
I use the ImportExcel PowerShell module for this script,
Install-Module -Name ImportExcelBefore proceeding further, make sure you have the Teams PowerShell module installed. You’ll need to run this script with Teams Administrator role.
$TeamsCred = Get-Credential
Connect-MicrosoftTeams -credential $TeamsCred
$xlsxPath = ".\Teams-Report_$((Get-Date).ToString("MMddyyyy")).xlsx"
Get-Team | Select GroupId,DisplayName,MailNickName,Archived,Visibility,Description | foreach {
$ID = $_.GroupId
$TeamName = $_.DisplayName
$NickName = $_.MailNickName
$Archived = $_.Archived
$visibility = $_.Visibility
$Description = $_.Description
$ch = Get-TeamChannel -GroupId $ID
$ChannelCount = $ch.count
$TeamUser = Get-TeamUser -GroupId $ID
$TeamMemberCount = $TeamUser.Count
$TeamOwnerCount = ($TeamUser | ?{$_.role -eq "owner"}).count
$stdchannelCount = ($ch | ?{$_.MembershipType -eq "Standard"}).count
$privchannelCount = ($ch | ?{$_.MembershipType -eq "Private"}).count
[PSCustomObject]@{
'Teams Name'=$TeamName;
'Teams MailNickName'=$NickName;
'Teams Type'=$Visibility;
'Description'=$Description;
'Archived?'=$Archived;
'Channel Count'=$ChannelCount;
'Standard Channel Count'=$stdchannelCount;
'Private Channel Count'=$privchannelCount;
'Team Members Count'=$TeamMemberCount;
'Team Owners Count'=$TeamOwnerCount} | Export-Excel -Path $xlsxPath -WorksheetName "All Teams Report" -TableStyle Medium16 -AutoSize -Append
}
Get-Team | foreach {
$ID = $_.GroupId;
$TeamName = $_.DisplayName;
$NickName = $_.MailNickName;
Get-TeamUser -GroupId $ID | Select User,Name,Role |
Foreach {
[PSCustomObject]@{
'Teams ID' = $ID;
'Teams Name' = $TeamName;
'Teams MailNickName' = $NickName;
'User UPN' = $_.User;
'User DisplayName' = $_.Name;
'Role' = $_.Role
}
}
} | Export-Excel -Path $xlsxPath -WorksheetName "Teams_users" -TableStyle Medium16 -AutoSize
Get-Team | Foreach {
$ID = $_.GroupId;
$TeamName = $_.DisplayName;
$NickName = $_.MailNickName;
Get-TeamChannel -GroupId $ID | Select Id, DisplayName, MembershipType |
Foreach {
[PSCustomObject]@{
'Teams ID' = $ID;
'Teams Name' = $TeamName;
'Teams MailNickName' = $NickName;
'Channel Name' = $_.DisplayName;
'Channel Type' = $_.MembershipType
}
}
} | Export-Excel -Path $xlsxPath -WorksheetName "Channels" -TableStyle Medium16 -AutoSize
Get-Team | Foreach {
$ID = $_.GroupId;
$TeamName = $_.DisplayName;
$NickName = $_.MailNickName;
Get-TeamChannel -GroupId $ID | Select DisplayName |
Foreach {
$chName = $_.DisplayName;
Get-TeamChannelUser -GroupId $ID -DisplayName $chName | Select User,Name,Role |
Foreach {
[PSCustomObject]@{
'Teams Name' = $TeamName;
'Channel Name' = $chName;
'User UPN' = $_.User;
'User DisplayName' = $_.Name;
'User Role' = $_.Role
}
}
}
} | Export-Excel -Path $xlsxPath -WorksheetName "Channel_Users" -TableStyle Medium16 -AutoSize
Get-Team | foreach {
$nickName = $_.MailNickName
Get-Team -MailNickName $nickName | Select -Property * |
Foreach {
[PSCustomObject]@{
'Teams ID' = $_.GroupId;
'Teams Display Name' = $_.DisplayName;
'Teams MailNickName' = $nickName;
'Giphy Allowed?' = $_.AllowGiphy;
'Giphy Content Rating' = $_.GiphyContentRating;
'Allow Stickers And Memes' = $_.AllowStickersAndMemes;
'Allow Custom Memes' = $_.AllowCustomMemes;
'Allow Guest to Create & Update Channels' = $_.AllowGuestCreateUpdateChannels;
'Allow Guest to Delete Channels' = $_.AllowGuestDeleteChannels;
'Allow Members to Create & Update Channels' = $_.AllowCreateUpdateChannels;
'Allow Members to Create Private Channels' = $_.AllowCreatePrivateChannels;
'Allow Members to Delete Channels' = $_.AllowDeleteChannels;
'Allow Members to Add & Remove Apps'= $_.AllowAddRemoveApps;
'Allow Members to Create Update Remove tabs' = $_.AllowCreateUpdateRemoveTabs;
'Allow Members to Create Update Remove Connectors' = $_.AllowCreateUpdateRemoveConnectors;
'Allow Members to Edit Messages' = $_.AllowUserEditMessages;
'Allow Members to Delete Messages' = $_.AllowUserDeleteMessages;
'Allow Owner to Delete Messages' = $_.AllowOwnerDeleteMessages;
'Allow Team Mentions' = $_.AllowTeamMentions;
'Allow Channel Mentions' = $_.AllowChannelMentions;
'Show In Teams Search & Suggestions' = $_.ShowInTeamsSearchAndSuggestions
}
}
} | Export-Excel -Path $xlsxPath -WorksheetName "Teams_permissions" -TableStyle Medium16 -AutoSizeHope this script was helpful in determining the current state of your Teams deployment.
Thank you for stopping by. ✌