In Active Directory, When we open properties of an user account, click the Account tab, and then either check or uncheck boxes in the Account options dialog box, numerical values are assigned to the UserAccountControl attribute. This UserAccountControl attribute determines the state of an account in the AD domain: active or locked, Password change at the next logon is enabled or not, if users can change their passwords and other options.
Table of Contents
UserAccountControl Attribute in AD
To view user accounts,
- Click Start –> Programs
- Open Administrative Tools
- Click Active Directory Users and Computers
- Or run dsa.msc from run window
- Search for a user and right-click and select Properties
- Click on Account tab

The Account Options section has the following options,
- User must change password at next logon
- User cannot change password
- Password never expires
- Store password using reversible encryption
- Account is disabled
- Smart card is required for interactive logon
- Account is sensitive and cannot be delegated
- User Kerberos DES encryption types for this account
- This account supports Kerberos AES 128 bit encryption
- This account supports Kerberos AES 256 bit encryption
- Do not require Kerberos preauthentication
Each of these user account options is 1 (True) or 0 (False) and are not stored as separate AD attributes, instead the UserAccountControl attribute is used. The flags are cumulative. The total value of all options are stored in the value of UserAccountControl attribute.
To determine the current value of the attribute,
Using PowerShell,
$user = Read-Host "Enter user's logon"
Get-ADuser $user -properties * | Select name, UserAccountControl | ft
Using dsa.msc,
- dsa.msc from Run window
- Search for a user and right-click and select Properties
- Click on Attribute Editor tab
- If you are missing this tab, Click View in the Active Directory Users and Computers window and select Advanced Features
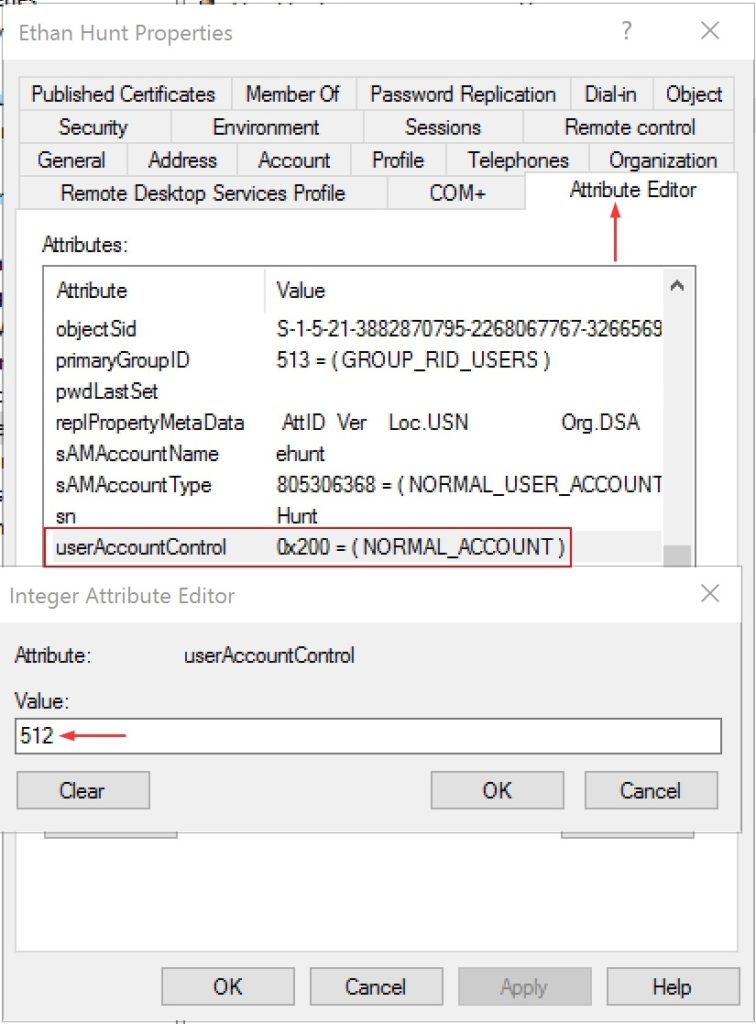
In this example, the value of the attribute is 0x200 (decimal value is 512).
The following table lists possible flags that can be assigned to an account. Each flag corresponds to a certain UserAccountControl bit, and UserAccountControl value equals the sum of all flags.
| UserAccountControl Flag | Hexadecimal Value | Decimal Value |
| SCRIPT | 0x0001 | 1 |
| ACCOUNTDISABLE | 0x0002 | 2 |
| HOMEDIR_REQUIRED | 0x0008 | 8 |
| LOCKOUT | 0x0010 | 16 |
| PASSWD_NOTREQD | 0x0020 | 32 |
| PASSWD_CANT_CHANGE | 0x0040 | 64 |
| ENCRYPTED_TEXT_PWD_ALLOWED | 0x0080 | 128 |
| TEMP_DUPLICATE_ACCOUNT | 0x0100 | 256 |
| NORMAL_ACCOUNT | 0x0200 | 512 |
| INTERDOMAIN_TRUST_ACCOUNT | 0x0800 | 2048 |
| WORKSTATION_TRUST_ACCOUNT | 0x1000 | 4096 |
| SERVER_TRUST_ACCOUNT | 0x2000 | 8192 |
| DONT_EXPIRE_PASSWORD | 0x10000 | 65536 |
| MNS_LOGON_ACCOUNT | 0x20000 | 131072 |
| SMARTCARD_REQUIRED | 0x40000 | 262144 |
| TRUSTED_FOR_DELEGATION | 0x80000 | 524288 |
| NOT_DELEGATED | 0x100000 | 1048576 |
| USE_DES_KEY_ONLY | 0x200000 | 2097152 |
| DONT_REQ_PREAUTH | 0x400000 | 4194304 |
| PASSWORD_EXPIRED | 0x800000 | 8388608 |
| TRUSTED_TO_AUTH_FOR_DELEGATION | 0x1000000 | 16777216 |
| PARTIAL_SECRETS_ACCOUNT | 0x04000000 | 67108864 |
The userAccountControl value is calculated as,
NORMAL_ACCOUNT (512) + ACCOUNTDISABLE (2) = 514
NORMAL_ACCOUNT (512) + DONT_EXPIRE_PASSWORD (65536) + ACCOUNTDISABLE (2) = 66050
To list all active users,
Get-ADUser -Properties * -ldapFilter "(useraccountcontrol=512)" | Select UserPrincipalName,userAccountControl | ftTo list all disabled user accounts,
Get-ADUser -Properties * -ldapFilter "(useraccountcontrol=514)" | Select UserPrincipalName,userAccountControl | ftTo list accounts with a non-expiring password,
Get-ADUser -Properties * -ldapFilter "(useraccountcontrol=66048)" | Select UserPrincipalName,userAccountControl | ftHere are the default UserAccountControl values for the certain objects:
- Typical user: 0x200 (512)
- Domain controller: 0x82000 (532480)
- Workstation/server: 0x1000 (4096)
Decode UserAccountControl Values
To fully decode UserAccountControl bit field we can use this PowerShell script,
Add-Type -TypeDefinition @'
[System.Flags]
public enum UserAccountControl{
SCRIPT = 1,
ACCOUNTDISABLE = 2,
BIT_02 = 4,
HOMEDIR_REQUIRED = 8,
LOCKEDOUT = 16,
PASSWD_NOTREQD = 32,
PASSWD_CANT_CHANGE = 64,
ENCRYPTED_TEXT_PWD_ALLOWED = 128,
TEMP_DUPLICATE_ACCOUNT = 256,
NORMAL_ACCOUNT = 512,
BIT_10 = 1024,
INTERDOMAIN_TRUST_ACCOUNT = 2048,
WORKSTATION_TRUST_ACCOUNT = 4096,
SERVER_TRUST_ACCOUNT = 8192,
BIT_14 = 16384,
BIT_15 = 32768,
DONT_EXPIRE_PASSWORD = 65536,
MNS_LOGON_ACCOUNT = 131072,
SMARTCARD_REQUIRED = 262144,
TRUSTED_FOR_DELEGATION = 524288,
NOT_DELEGATED = 1048576,
USE_DES_KEY_ONLY = 2097152,
DONT_REQ_PREAUTH = 4194304,
PASSWORD_EXPIRED = 8388608,
TRUSTED_TO_AUTH_FOR_DELEGATION = 16777216,
PARTIAL_SECRETS_ACCOUNT = 67108864
}
'@Which can be used like this to decode the bits,

If you want to display all flags that are set in UAC,
Get-AdUser -Filter * -Properties UserAccountControl | select name, @{n='UAC';e={[UserAccountControl]$_.UserAccountControl}}
This script can also be used to determine UserAccountControl value for specific AD accounts,
$user = Read-Host "Enter user's logon"
Get-ADuser $user -properties * | select name,UserPrincipalName, @{n='UAC';e={[UserAccountControl]$_.UserAccountControl}}
Update UserAccoutControl Attribute in AD using PowerShell
To change UserAccountControl attribute in AD using PowerShell, we can use Set-ADUser, Set-ADComputer and Set-ADAccountControl cmdlets,
$user = Read-Host "Enter user's logon"
Set-ADAccountControl -Identity $user –CannotChangePassword:$true -PasswordNeverExpires:$trueor
$user = Read-Host "Enter user's logon"
Set-ADUser -Identity $user –CannotChangePassword:$true -PasswordNeverExpires:$trueSet a specified computer to be trusted for delegation,
$Computer = Read-Host "Enter computer or server name"
Set-ADAccountControl -Identity $Computer -TrustedForDelegation $Trueor
$Computer = Read-Host "Enter computer or server name"
Set-ADComputer -Identity $Computer -TrustedForDelegation $TrueThe user account attribute can also be updated using the Set-ADUser cmdlet. In this below example, I’m enabling user account,
$user = Read-Host "Enter user's logon"
Set-ADUser $user -Replace @{UserAccountControl = 512}Hope this post helped you get a better understanding of the UserAccountControl attribute.
Thank you for stopping by ✌