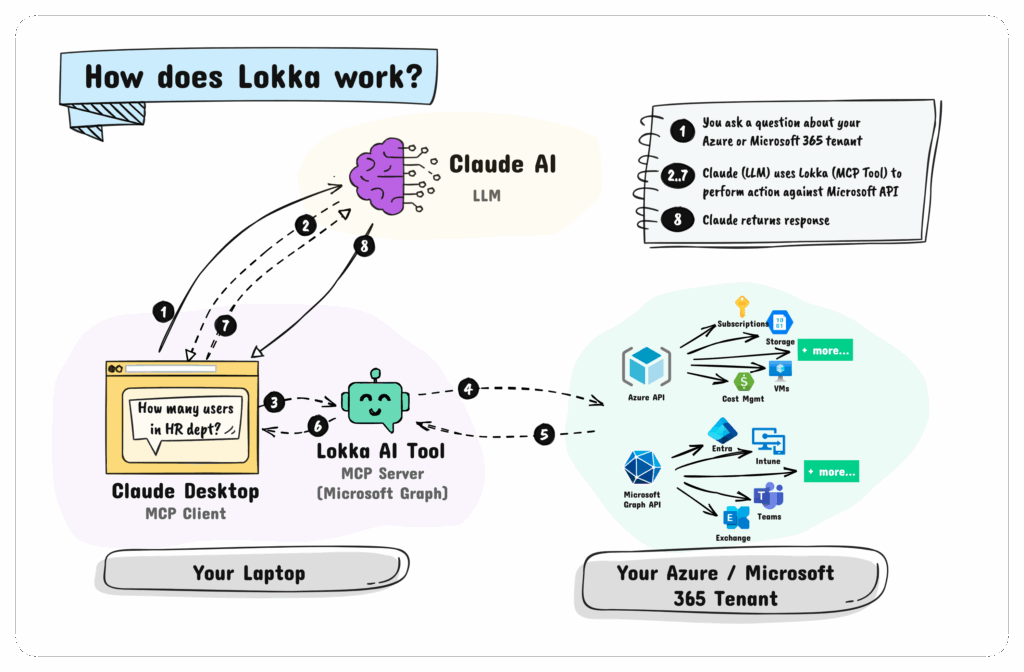
Let’s cut to the chase, cloud access control isn’t just a checkmark on your compliance list anymore. It’s a daily battlefield. With global teams, hybrid workloads, and rising security risks, who can do what and under what conditions is now a core pillar of IT strategy.
If you’re working in Azure, you’ve likely heard of RBAC (Role-Based Access Control) and ABAC (Attribute-Based Access Control). But what you may not know is that these aren’t mutually exclusive instead they’re better together.
Let’s unpack what each model does, where they shine (and struggle), and how to combine them for airtight, scalable access governance in Azure.
What is Azure Role-Based Access Control (RBAC)?
Azure RBAC helps you control access by assigning roles to security principals (users, groups, service principals, or managed identities) at a specific scope (subscription, resource group, or resource).
Each role is a bundle of permissions, think of them as job descriptions for Azure resources.
Example RBAC Use Cases
- A user who can manage only virtual machines in the
Devsubscription. - A group assigned the Reader role at the resource group level.
- An app given Contributor access to only one storage account.
RBAC works well when your access needs are role-based and relatively straightforward. But as organizations scale and become more dynamic, things can get messy fast.
Where RBAC Falls Short
RBAC starts to creak when:
- You need to create roles for every unique mix of region, team, and resource.
- You end up with a Frankenstein monster of roles like:
VP - EuropeManager - AsiaSalesRep - NorthAmerica - Junior
- You have hierarchical or multi-tenant data structures that don’t fit RBAC’s flat model.
The result? Role sprawl, administrative pain, and security gaps.
What is Azure Attribute-Based Access Control (ABAC)?
ABAC adds contextual smarts to access control. Instead of relying solely on roles, it factors in attributes of:
- The user (e.g., department = HR)
- The resource (e.g., tag = Project:Alpine)
- The environment (e.g., access during business hours only)
In Azure, ABAC is implemented through role assignment conditions that filter RBAC permissions.
ABAC in Action
- “Chandra can read blobs only if they’re tagged with
Project=Cascade.” - “Support engineers can impersonate users only during a help session.”
- “Users can access data only in their assigned region or cost center.”
This kind of fine-grained access is powerful, flexible, and crucial in multi-tenant, regulated, or fast-moving environments.
RBAC + ABAC: Not a Choice – A Collaboration
Here’s the mindset shift: RBAC and ABAC are not competing models. They’re complementary.
RBAC defines what actions are allowed.
ABAC defines under what conditions those actions are allowed.
By combining the two, you can:
- Keep your role structure simple and understandable.
- Layer on access conditions that reflect real-world business rules.
Common Hybrid Patterns
| Scenario | RBAC Role | ABAC Condition |
|---|---|---|
| Multi-tenant app | Tenant Admin | Only for tenant_id=X |
| Regional access | Sales Manager | Region = “North America” |
| Subscription tiers | Premium User | Access feature only if plan=premium |
| File access | Editor | Only owner=user_id or shared_with=user_id |
| Support scenarios | Support Agent | Impersonation allowed if user_in_session=true |
Best Practices for RBAC and ABAC in Azure
Let’s bring it home with the golden rules:
RBAC Best Practices
- Least Privilege Always: Grant only the permissions needed—nothing more.
- Limit Subscription Owners: Three max. The fewer, the safer.
- Use PIM for Just-in-Time Access: With Microsoft Entra PIM, elevate access temporarily.
- Assign Roles to Groups: Not individuals. Makes scaling and auditing easier.
- Avoid Wildcards in Custom Roles: Be explicit with
ActionsandDataActions. - Script with Role IDs, Not Names: Avoid breakage from renamed roles.
ABAC Best Practices
- Tag Strategically: Use meaningful tags like
Project,Environment, orClassificationto enable ABAC. - Use Conditions to Reduce Role Sprawl: Filter access with precision.
- Start Small: Pilot with blob storage conditions before scaling ABAC elsewhere.
- Don’t Replace RBAC: Use ABAC as a filter, not a replacement.
Recap: When to Use What
| Feature | RBAC | ABAC | RBAC + ABAC |
|---|---|---|---|
| Simplicity | ✅ | ❌ | ✅ |
| Contextual Flexibility | ❌ | ✅ | ✅ |
| Scalability | ⚠️ (sprawl risk) | ✅ | ✅ |
| Multi-Tenant Scenarios | ⚠️ | ✅ | ✅ |
| Least Privilege Enforcement | ✅ | ✅ | ✅✅ |
Final Thoughts
RBAC gives you structure. ABAC gives you nuance. In Azure, using both gives you power and precision.
Don’t fall into the “either/or” trap. The real magic happens when you combine the predictability of RBAC with the intelligence of ABAC to build access models that scale with your business.
Thanks for stopping by. ✌