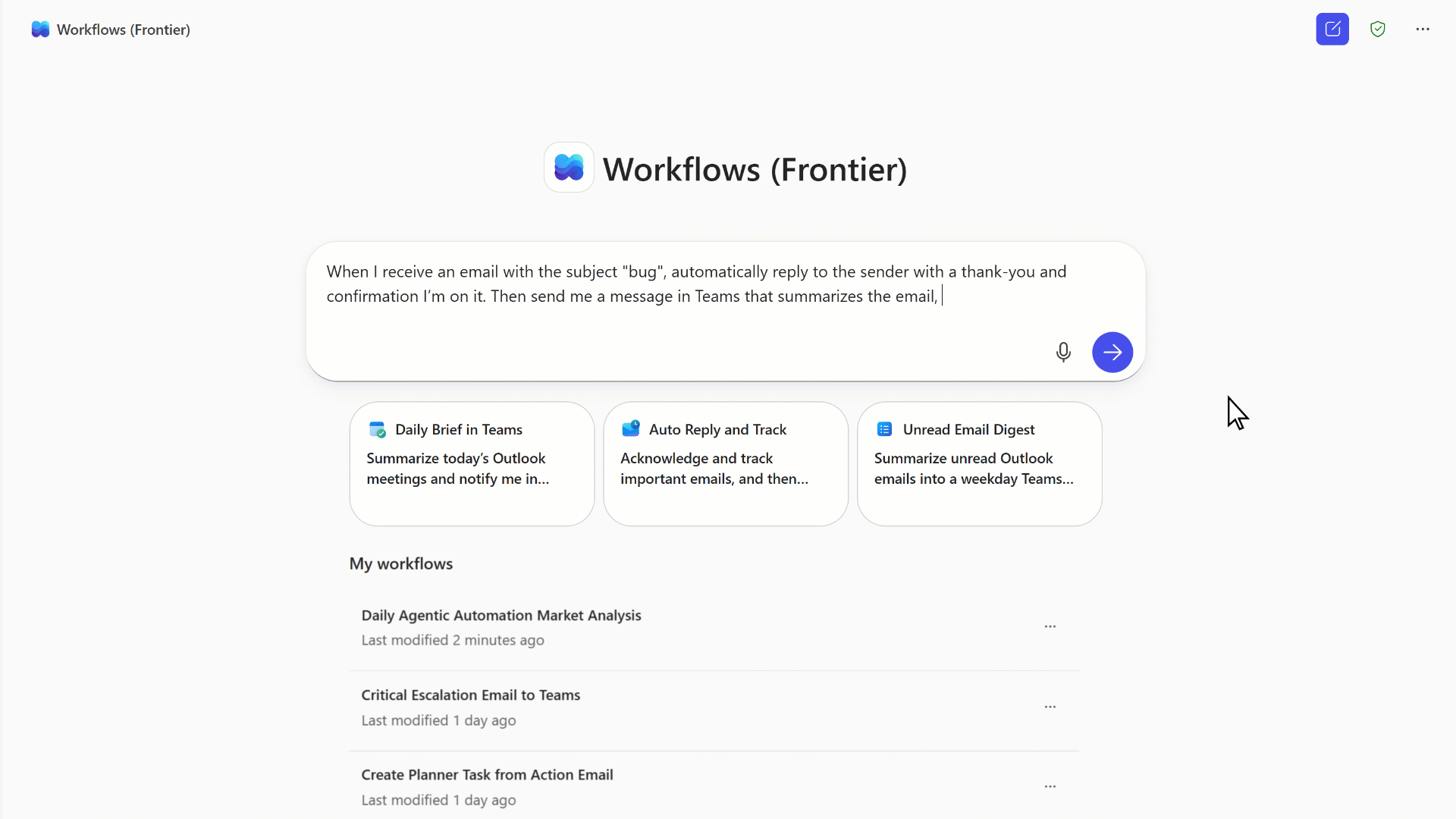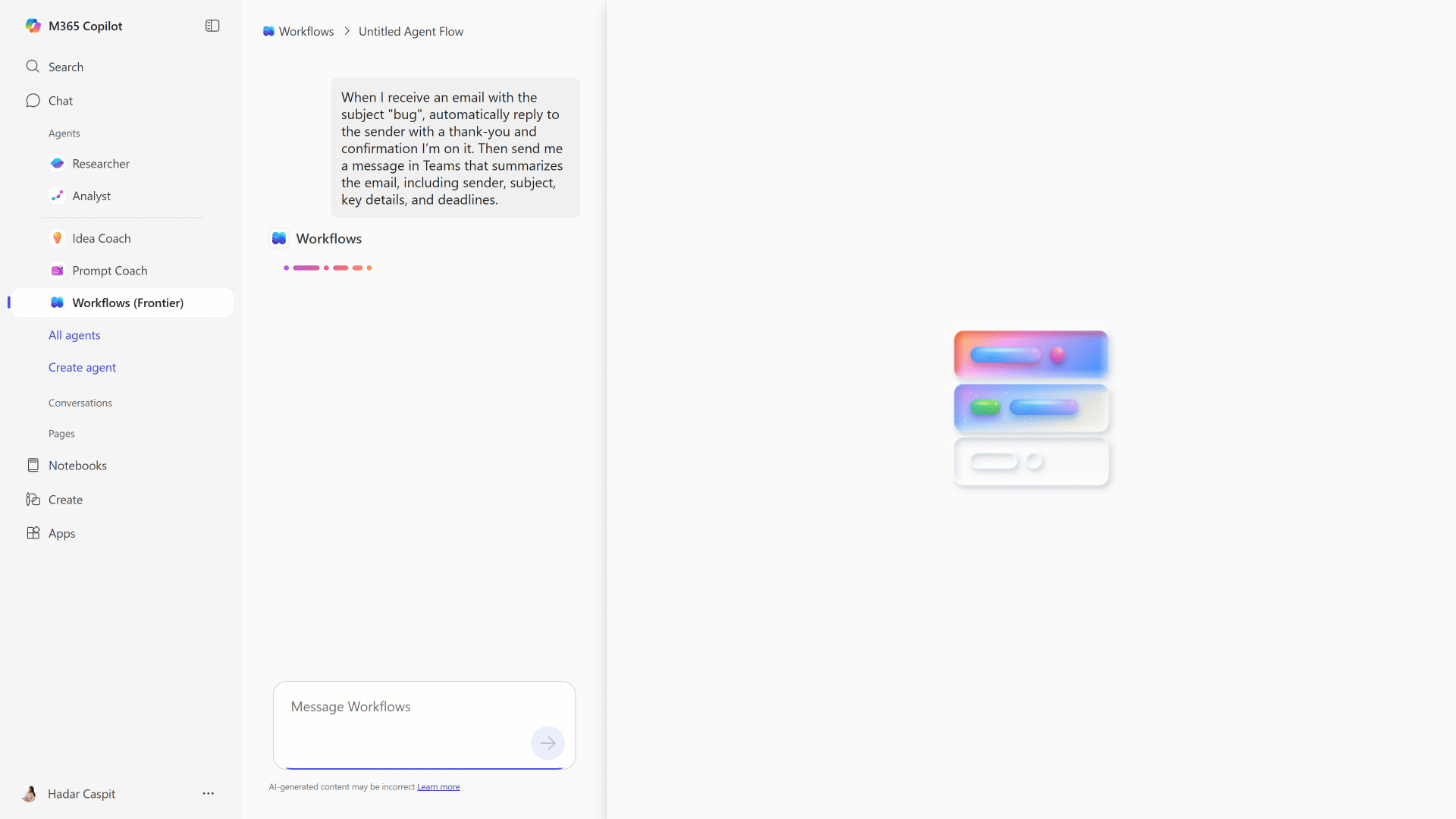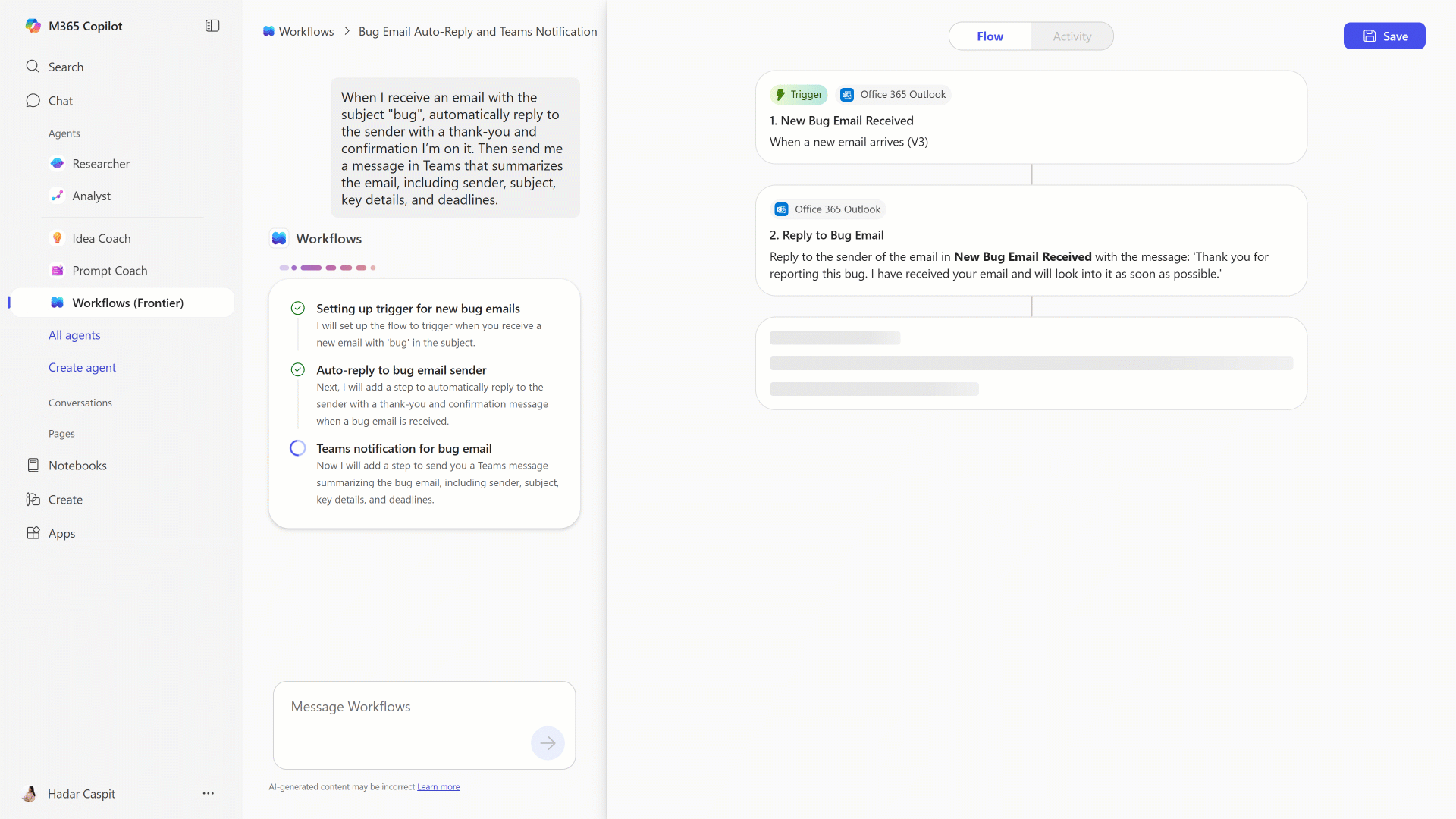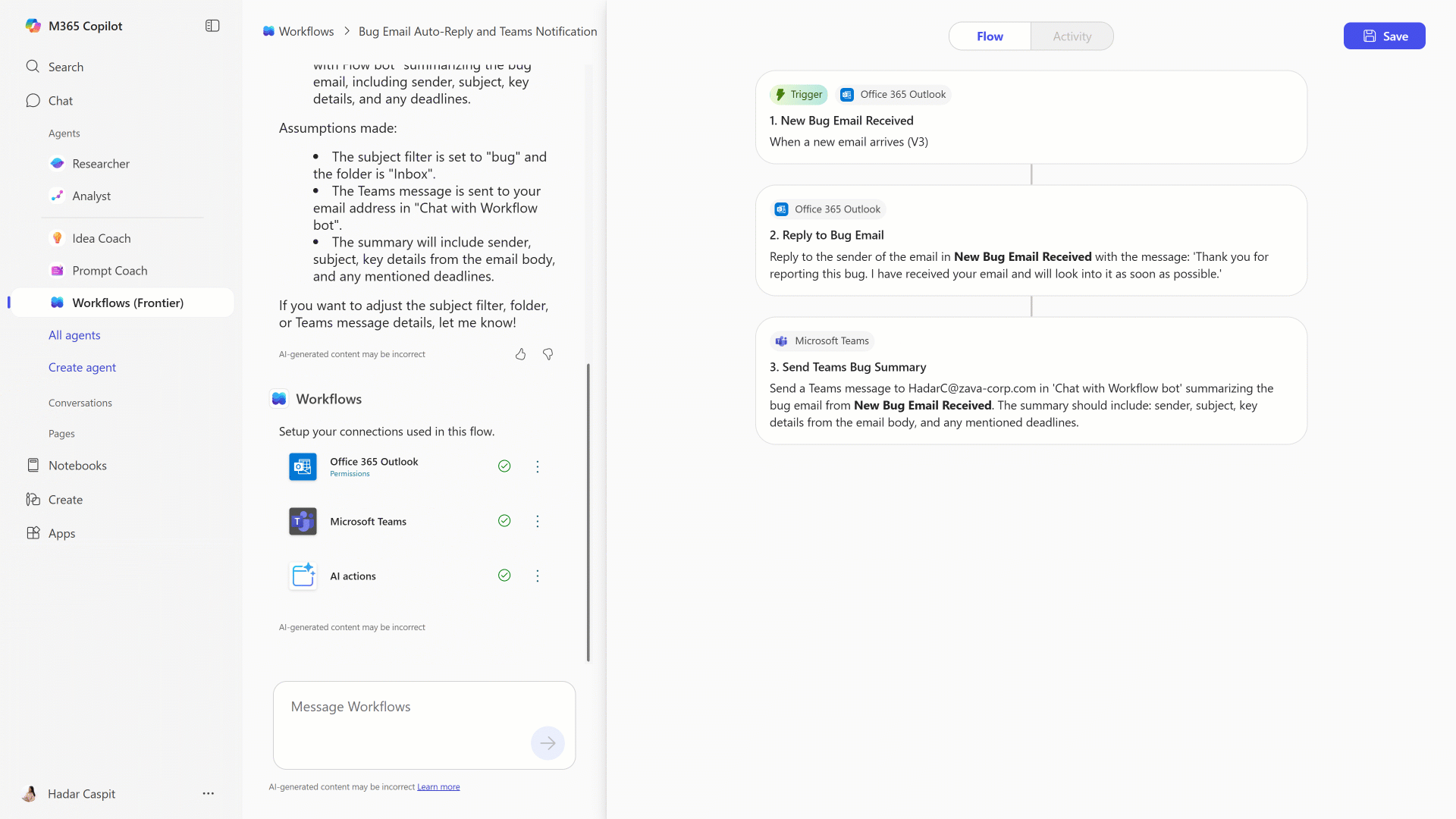
December is usually the month where admins brace for year-end freezes… but Microsoft apparently didn’t get the memo. This month’s wave of updates brings retirements, new capabilities, compliance upgrades, and several “fix this or something breaks” action items for enterprise tenants.
As 2025 comes to a close, Microsoft is rolling out a series of final updates that reinforce its focus on data governance, AI-powered productivity, and secure-by-default principles. With key feature retirements, new security protections in Teams, and compliance tools being supercharged, December is far from a quiet month for Microsoft 365 admins.
Whether you manage collaboration, security, data lifecycle, or compliance, this guide covers the critical retirements, new features, enhancements, and action items rolling out this month.

December at a Glance
| Category | Count |
|---|---|
| 🔻 Retirements | 6 |
| 🆕 New Features | 12 |
| 🔧 Enhancements | 8 |
| 🔄 Functionality Changes | 3 |
| ⚠️ Action Required | 3 |
Retirements: Cleanup Season Arrives for Legacy Features
Favorite Contacts Retires in Microsoft Places
Early December marks the retirement of the Favorite Contacts experience in Microsoft Places, replaced with the more consistent Frequent Contacts model used across other apps. Admins also lose the related PowerShell control.
🔗 Learn more:
https://admin.cloud.microsoft/?#/MessageCenter/:/messages/MC1182693
App Skills Retired in Copilot for Excel
Microsoft is removing App Skills from Copilot for Excel and promoting Agent Mode as the new standard for in-workbook insights. Copilot Chat remains the recommended fallback.
🔗 Reference:
https://admin.cloud.microsoft/?#/MessageCenter/:/messages/MC1184407
TeamworkDevice (Beta) API Removed From Microsoft Graph
The TeamworkDevice (beta) Graph API will be retired on Dec 8, 2025. Device management now routes through the Teams Rooms Pro Management Portal.
🔗 Details:
https://admin.cloud.microsoft/?#/MessageCenter/:/messages/MC1183294
PowerPoint “Reuse Slides” Feature Retired
The well-loved Reuse Slides feature disappears from PowerPoint for Windows and Mac this month. Users must manually copy/paste slides after the removal.
🔗 Details:
https://admin.cloud.microsoft/?#/MessageCenter/:/messages/MC1179161
End of Support for Teams on Android 8
By late December, Microsoft will no longer provide security patches or bug fixes for Teams on Android 8 devices.
🔗 More info:
http://admin.cloud.microsoft/?#/MessageCenter/:/messages/MC1181212
Assignments & Courses ACEs Retired in Viva Connections/SharePoint
Education tenants should prepare for the retirement of Assignments and Courses ACEs on Dec 31, 2025, with end of support coming June 30, 2026.
🔗 Announcement:
https://admin.cloud.microsoft/?#/MessageCenter/:/messages/MC1184647
New Features: High-Impact Enhancements You’ll Want to Enable
Priority Cleanup for Purview Data Lifecycle Management
A powerful new capability allows admins to delete OneDrive and SharePoint content even if retention or legal holds apply, ideal for high-volume items like meeting recordings.
🔗 Feature documentation:
https://learn.microsoft.com/en-us/purview/priority-cleanup-exchange
Tenant-owned Domain Impersonation Detection in Teams
Teams will now automatically warn users when external senders use look-alike domains (e.g., “c0ntoso.com”), a major uplift in external collaboration protection.
🔗 Message Center:
https://admin.cloud.microsoft/?#/MessageCenter/:/messages/MC1187679
More Accurate Presence for Teams on the Web
Teams presence will finally behave intelligently in the browser by tracking device activity, not just active tabs.
🔗 Info:
https://admin.cloud.microsoft/?#/MessageCenter/:/messages/MC1184412
Cost Estimator & Transparency Reports for Data Security Investigations
Purview now offers a lightweight cost estimator and a billing usage dashboard for DSI workloads.
🔗 Reference:
https://admin.cloud.microsoft/?#/MessageCenter/:/messages/MC1186360
Automatic Work Location Based on Wi-Fi
Teams can automatically set a user’s work location when connecting to company Wi-Fi.
🔗 Roadmap item:
https://www.microsoft.com/en-US/microsoft-365/roadmap?filters=&searchterms=488800
Integration of Insider Risk & Data Security Investigation
Admins can now launch a pre-scoped DSI directly from an Insider Risk case, streamlining investigations.
🔗 Roadmap item:
https://www.microsoft.com/en-us/microsoft-365/roadmap?filters=&searchterms=501781
Microsoft 365 Backup Activity Logging
Backup policy changes and restore events will now surface in Microsoft 365 monitoring logs.
🔗 Roadmap:
https://www.microsoft.com/en-US/microsoft-365/roadmap?filters=&searchterms=500019
Actionable DLP Email Notifications
Users can now remediate DLP violations directly from email alerts: stop sharing, delete files, apply labels, and more.
🔗 Roadmap:
https://www.microsoft.com/en-US/microsoft-365/roadmap?filters=&searchterms=464996
PST Import Support for the New Outlook
Admins rejoice: PST import is coming to the new Outlook, easing migrations and mailbox recovery work.
🔗 Roadmap:
https://www.microsoft.com/en-US/microsoft-365/roadmap?filters=&searchterms=485739
ChatGPT Enterprise Connector Integration with Purview
Organizations can now collect and review ChatGPT Enterprise prompt/response logs within Purview.
🔗 Roadmap:
https://www.microsoft.com/en-us/microsoft-365/roadmap?filters=&searchterms=401125
eDiscovery Premium Support for Non-M365 Data
Review sets in eDiscovery Premium will support non-Microsoft 365 content through direct import.
🔗 MC post:
https://admin.cloud.microsoft/?#/MessageCenter/:/messages/MC1176369
Enhancements: Improvements That Take Governance & Security Further
Sensitivity Label Group Modernization
Parent labels are being replaced by clean Label Groupings, reducing UI confusion.
🔗 Roadmap:
https://www.microsoft.com/en-US/microsoft-365/roadmap?filters=&searchterms=386900
Updated Identity Protection Alert Settings in Defender XDR
Starting Dec 11, admins can choose to ingest:
- High-risk alerts only
- High + Medium
- All detections
The default will shift to High-risk only.
🔗 Message Center:
https://admin.cloud.microsoft/?#/MessageCenter/:/messages/MC1190195
Organizational Messages Expanded to Hybrid-Joined Devices
Hybrid-joined endpoints now receive Organizational Messages alongside cloud-joined devices.
🔗 Roadmap:
https://www.microsoft.com/en-US/microsoft-365/roadmap?filters=&searchterms=503564
Insider Risk Management Scale Increases
Variants, detection group size, and total indicators get major increases for enterprises with high-volume signals.
🔗 Roadmap:
https://www.microsoft.com/en-US/microsoft-365/roadmap?filters=&searchterms=518291
Multiple DLP Policies as IRM Triggers
IRM can now listen for multiple DLP policies at the same time.
🔗 Roadmap:
https://www.microsoft.com/en-in/microsoft-365/roadmap?searchterms=493757
SMTP DANE with DNSSEC for Exchange Online (GCC High & DoD)
Better email authentication and routing security arrives for government cloud tenants.
🔗 Roadmap:
https://www.microsoft.com/en-in/microsoft-365/roadmap?featureid=361914&searchterms=361914
Microsoft 365 Backup for GCC
GCC tenants will gain access to Microsoft 365 Backup this month.
🔗 Roadmap:
https://www.microsoft.com/en-US/microsoft-365/roadmap?filters=&searchterms=494517
Planner Retention Support (Data Lifecycle Management)
Admins will be able to apply retention policies to Planner content, finally enabling compliance-grade lifecycle control.
🔗 Roadmap:
https://www.microsoft.com/en-US/microsoft-365/roadmap?filters=&searchterms=486828
Existing Functionality Changes: Updates You’ll Notice Immediately
Teams App Usage Report → Integrated Apps Usage Report
The redesigned report now includes Teams, Outlook, Microsoft 365 apps, and Copilot extensions.
🔗 Roadmap:
https://www.microsoft.com/en-in/microsoft-365/roadmap?id=410248
Intune Firewall Rules Updated (Azure Front Door)
Starting Dec 2, Intune endpoints shift to Azure Front Door IPs. Firewall allowlists must be updated.
🔗 Message Center:
https://admin.microsoft.com/Adminportal/Home#/MessageCenter/:/messages/MC1150664
SharePoint Agent Usage Stats Aggregated Tenant-wide
Instead of per-site views, SharePoint now aggregates usage statistics across the entire tenant.
🔗 Roadmap:
https://www.microsoft.com/en-US/microsoft-365/roadmap?filters=&searchterms=480729
Action Required: These Items Must Be Addressed Before Year-End
UKG & Blue Yonder Connectors in Teams Shifts Retired (Dec 7)
- UKG → migrate to UKG Flow
- Blue Yonder → build a custom integration
🔗 MC post:
https://admin.cloud.microsoft/?#/MessageCenter/:/messages/MC1166868
Visio Data Visualizer Add-in Removed from Excel (Dec 8)
Creation of new diagrams via the add-in ends December 8. Export existing files to .vsdx.
🔗 MC post:
https://admin.cloud.microsoft/?#/MessageCenter/:/messages/MC1182535
Mailbox Audit Log Cmdlets Retired (Late 2025)
Search-MailboxAuditLog and New-MailboxAuditLogSearch will be retired; use Search-UnifiedAuditLog instead.
🔗 TechCommunity post:
https://techcommunity.microsoft.com/blog/microsoft-security-blog/microsoft-exchange-online-search-mailboxauditlog-and-new-mailboxauditlogsearch-w/4366310
Final Thoughts: A Busy Month Sets the Tone for 2026
December 2025 is a fitting finale for the year, focused on resilience, risk mitigation, and refinement. AI is evolving, compliance tools are tightening, and the experience across M365 is becoming more predictable, governable, and secure.
- Review what’s retiring
- Enable new protections
- Prepare for shifting compliance baselines
- Communicate change to stakeholders
Stay sharp. Stay secure. Stay compliant.
Thank you for stopping by. ✌️